Details:
Subject: Re: UofT Personal Assistant ! Boidurjo Das
Phishing emails are designed to trick recipients into taking an action, such as clicking a malicious link or opening a malicious attachment. Hackers may also use tactics like smishing, which attempt to trick the recipients through text messages or SMS.
This week, members of the University of Toronto (U of T) community received an email impersonating U of T’s IT administration that asked recipients to respond through SMS. Please note that any technology upgrades or updates will always be communicated by your division or department through official U of T channels prior to deployment.
Sense of urgency is a big factor that hackers use to get recipients to take action. You will be able to identify and report phishing by taking a moment to review your emails for common red flags.
The image below marks the red flags to look out for:
Hackers are constantly adopting new techniques to steal information, so it is imperative that we stay alert and aware to better protect ourselves online.
Visit the Security Matters website for more information.
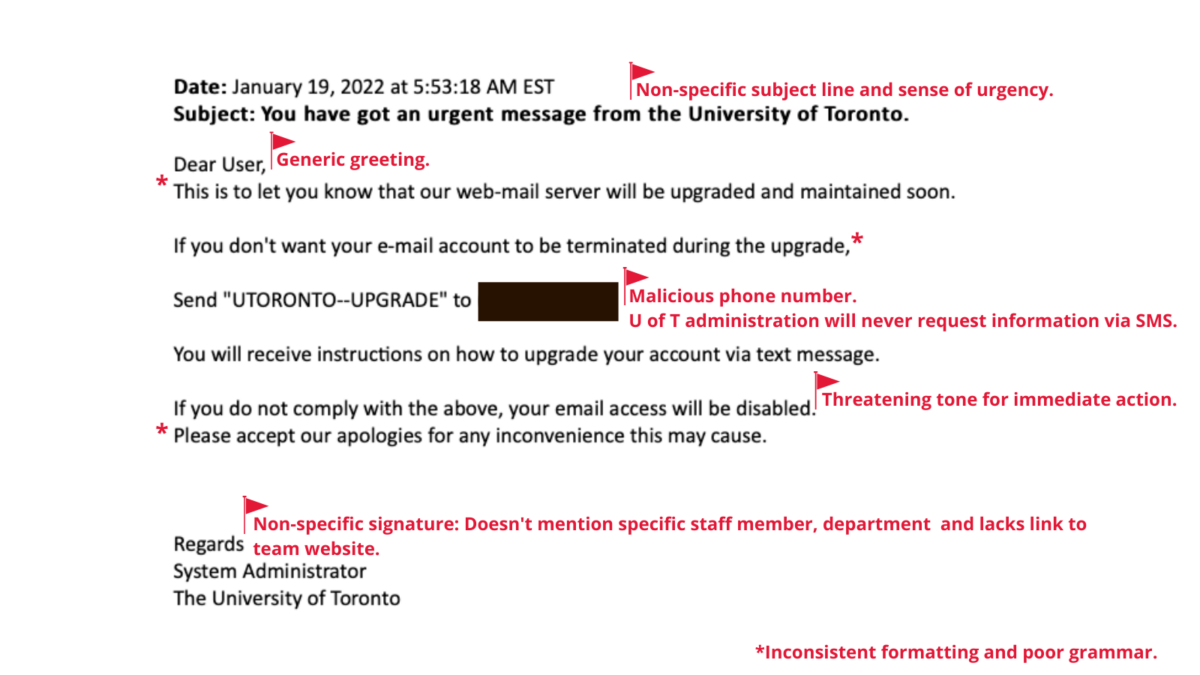
Subject: You have got an urgent message from the University of Toronto.
Dear User,
This is to let you know that our web-mail server will be upgraded and maintained soon.
If you don’t want your e-mail account to be terminated during the upgrade,
Send “UTORONTO–UPGRADE” to *malicious phone number inserted here*
You will receive instructions on how to upgrade your account via text message.
If you do not comply with the above, your email access will be disabled.
Please accept our apologies for any inconvenience this may cause.
Regards
System Administrator
The University of Toronto
Subject: 50141497*** Received -TSID: Powells WellCare Received on January 3, 2022, 3:22:33 PM
New Voicemail Received.
| Date received | Monday, January 03, 2022 |
|---|---|
| Caller Number | *Malicious number inserted here* |
| Duration | 00:00:54 |
| Reference | 1783-829-66312TD |
To listen to this voicemail, click on the attachment in this email.*Malicious link attached as voicemail*
Subject: You have got an urgent message from the University of Toronto.
Dear User,
This is to let you know that our web-mail server will be upgraded and maintained soon.
If you don’t want your e-mail account to be terminated during the upgrade,
Send “UTORONTO–UPGRADE” to *malicious phone number inserted here*
You will receive instructions on how to upgrade your account via text message.
If you do not comply with the above, your email access will be disabled.
Please accept our apologies for any inconvenience this may cause.
Regards
System Administrator
The University of Toronto
Subject: Open position:customer support representative, apply now.
A customer support representative position is available, with a decent weekly salary and the ability to work remotely.
*The job will only require 1-2 hours of your time every day, Monday through Friday or on weekends.
The ideal candidate will be dependable, timely, and trustworthy.
POSITION: customer support representative
SKILLS NEEDED
*Ability to work independently
*Basic computer knowledge
*To apply, text “Job application” to: *fake phone number inserted here*
Subject: [IMPORTANT]: University of Toronto recruiting department.
Hello Selected candidate,
We received your resume application via the University recruiting department, offering a part time position for Freshman, Sophomore, Junior, Senior, Graduating Students, Staff or retired, this will only require 1-2hrs 3 days a week, no work experience or skill is required. You can make $700 bi-weekly ( every two weeks )without affecting your regular activities and academics
To Apply, kindly follow the link or email/text below
*Malicious link inserted here*
*Fake name inserted here*
Tel: *fake phone number inserted here*
*Fake email address hyperlinked with malicious link inserted here*
Subject: Mail Update on 18 November, 2021
This message is from a trusted sender.
*Fake Office 365 inserted here*
1 Voicemail Message Received
You have receive 1 VoiceMail from a caller in your contact.
Date received: 18 November, 2021
Duration: 00:01:14
Message can only be accessed by *fake email address inserted here* after verifying the ownership.
Scanned File is safe to open.
*Fake McAfee Secure logo inserted here*
*Fake U of T web address*
Subject: Secure Notice on 11:47 AM, 16 Nov 2021
*Fake Microsoft logo inserted here*
Hello *recipient’s email inserted here*
Your Utoronto password is set to expire in 6 day(s).
*Recipient’s email inserted here*
We encourage you to take the time now to maintain your password activity to avoid login interruption.
*Malicious link inserted here*
Note: Microsoft will not be held responsible for any account loss
Thank you,
Copyright Utoronto 2021. All Rights Reserved.
Social engineering is designed to evade common security setups by targeting the people inside organizations — relying on human error as the weak link. While hackers’ approaches behind social engineering may differ in form, their goals are all very similar: identity theft, data breaches, ransomware attacks and more.
Phishing, one of the most popular forms of social engineering, is becoming more common with each day. It is very important to educate ourselves about cyber security to ensure our individual and institutional data remains protected. Equipping ourselves and the University of Toronto (U of T) with sophisticated and advanced tools is only half the battle. We can be proactive in preventing data breaches and other attacks by staying educated and aware, and therefore avoiding potential for human error.
Recently, there has been an influx of phishing emails containing malicious links targeted at U of T community members. These attacks have been impersonating U of T administrator roles and targeting unsuspecting community members.
Below are two recent emails that were sent to U of T community members. Review the red flags to help you understand the anatomy of a phishing email:
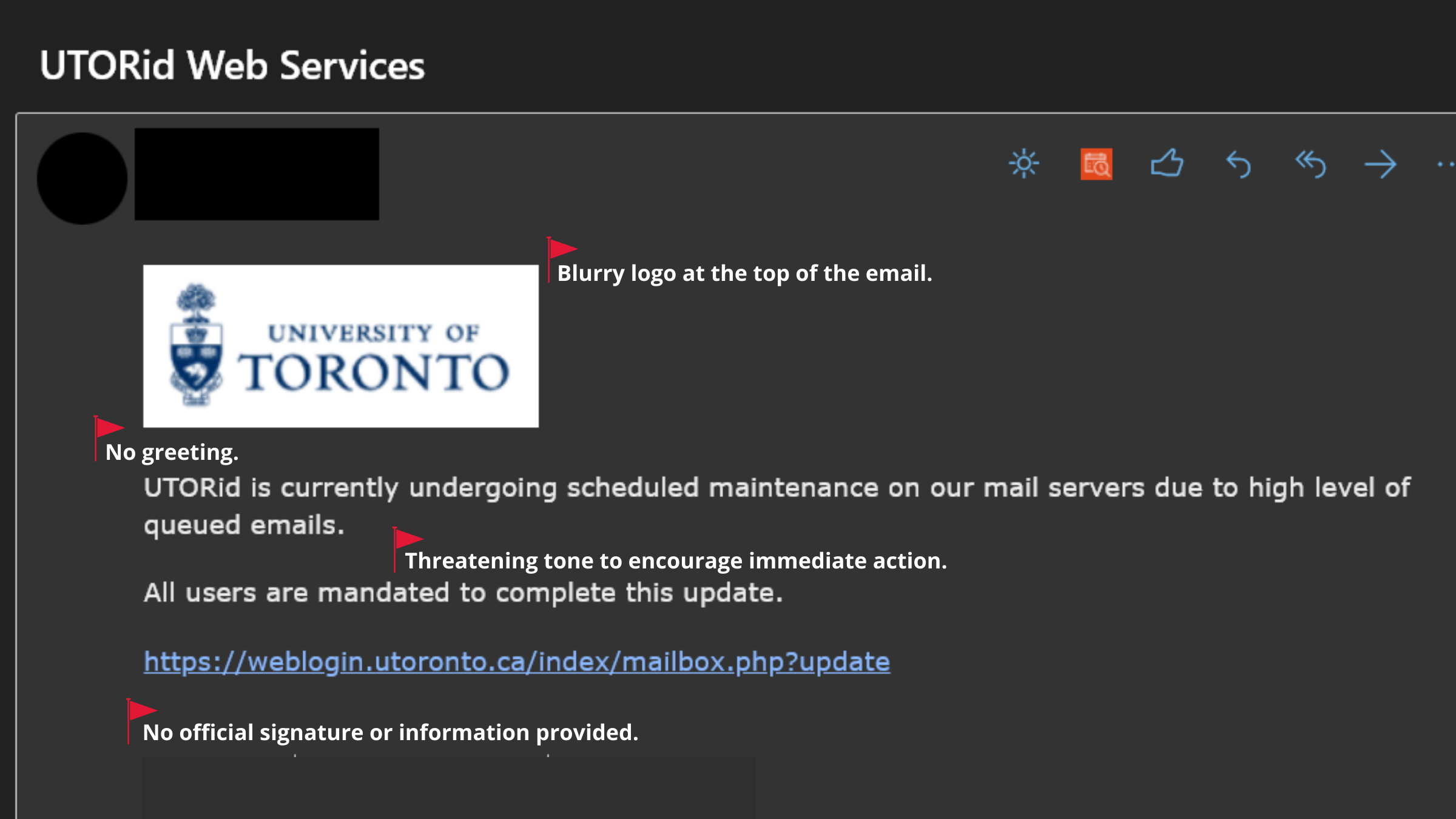
Image 1: This recent phishing email contains a malicious link to a spoofed UTORid web page. The email was sent from an email address impersonating a U of T staff member.
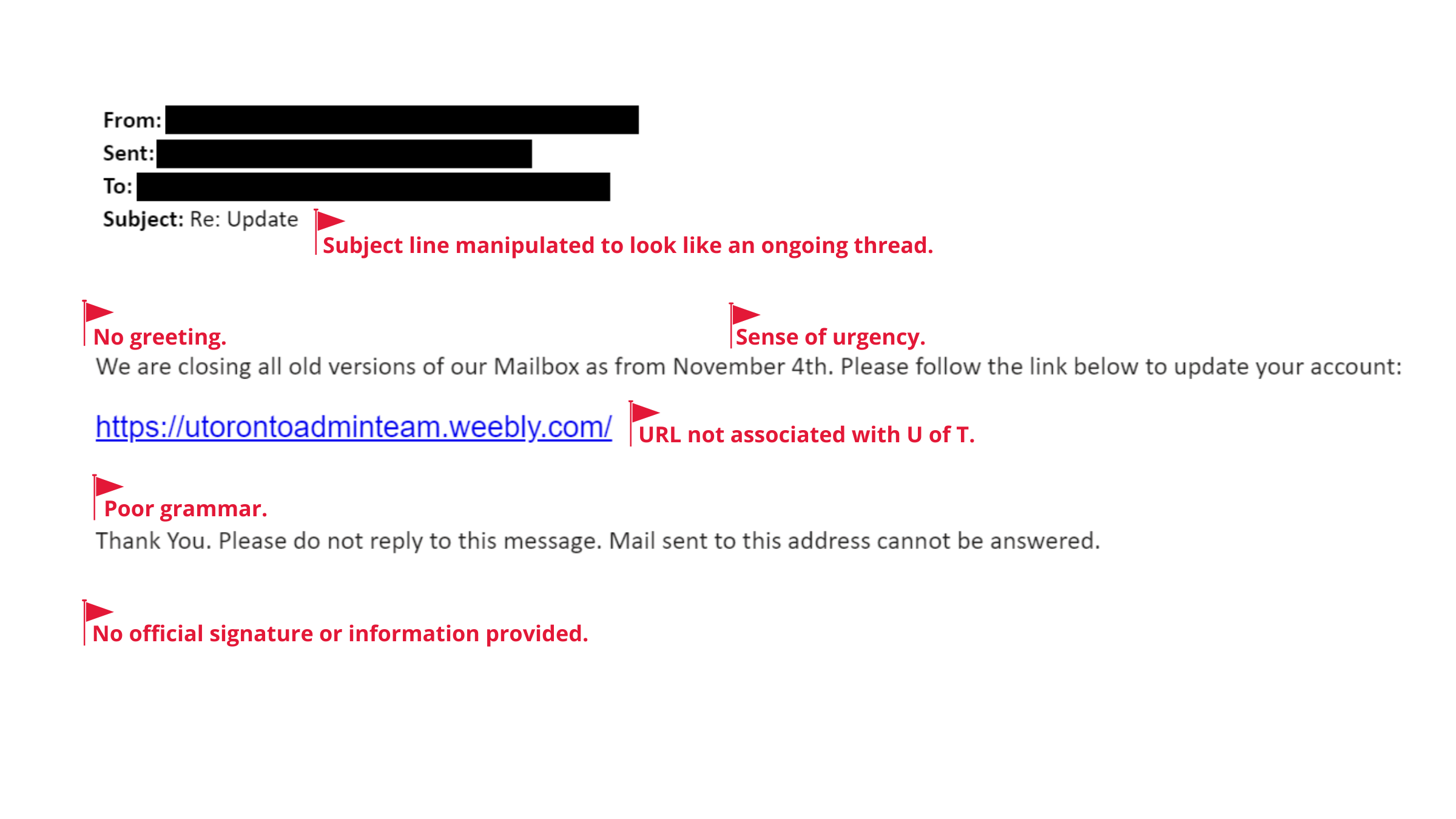
Image 2: This email prompts U of T community members to click on a link to ‘update their account’.
At first glance, phishing emails often look like legitimate communications from a trusted organization. No matter how real it looks, treat every email you receive with caution — especially ones you weren’t expecting to receive. In the case of receiving a suspicious email, review the common red flags to identify if action is required to report and remove the email.
If you receive a suspicious email, ensure you report and delete the email immediately.
For information on how to report a phish, visit https://securitymatters.utoronto.ca/report/.
Visit the Phish Bowl and the Security Matters blog to read about recent phishing attacks within the U of T community.