Access to a diverse range of data from sensitive personal information to confidential research data, has made the University of Toronto (U of T) a popular target for various cyber-threats including phishing.
Last week, more phishing attempts were reported as targeting the U of T community. The rising occurrence of phishing campaigns should serve as a reminder to stay aware and learn how to identify and report phishing.
Job scam emails
Job scam emails are crafted with the intent of gaining access to personal or institutional information. They are usually unsolicited and masquerade as employment offers to captivate the recipients’ interest. Often, hackers pretend to be from a well-known and legitimate company to convince recipients to respond to their email. These emails usually prompt recipients to reply to the message, click on a malicious link or download an attachment.
Unsolicited emails with employment offers that seem too good to be true should be treated with suspicion. Legitimate companies typically post vacancies with detailed job descriptions and department information on their official website or a trusted job search website. Qualified candidates are then contacted for interviews via official channels of communication.
Below are the two job scam emails that were sent to U of T community members. Review the emails to identify some of the red flags:
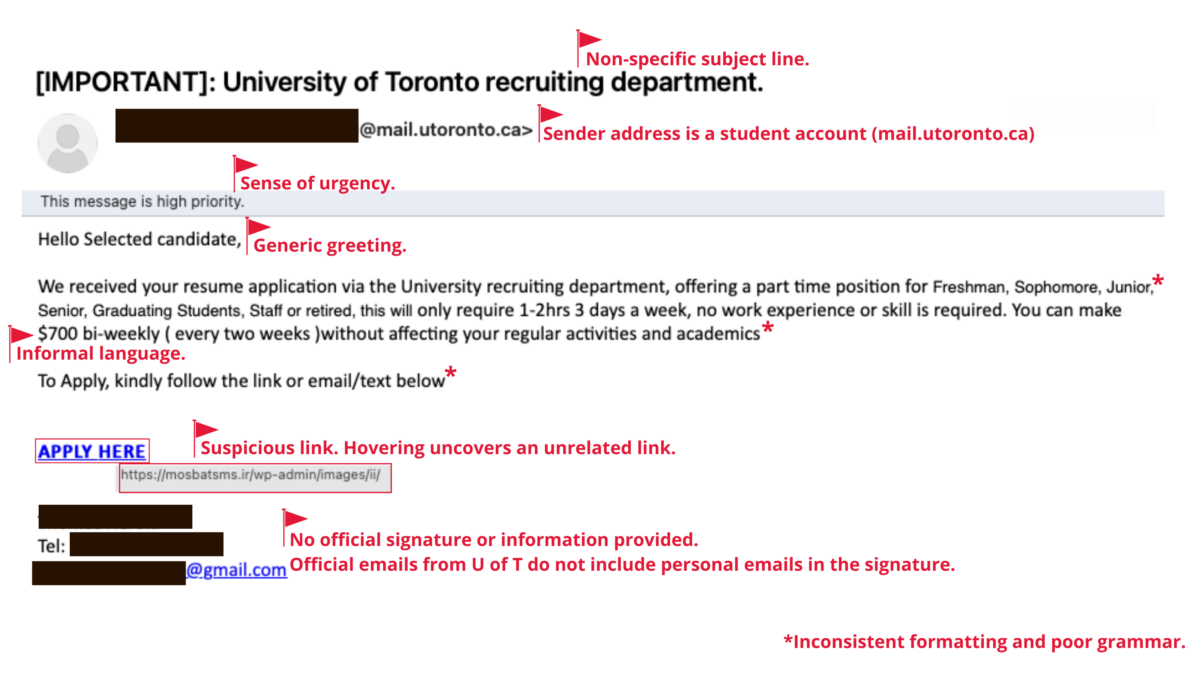
Image 1: This phishing email impersonates a U of T staff member and contains a malicious link.

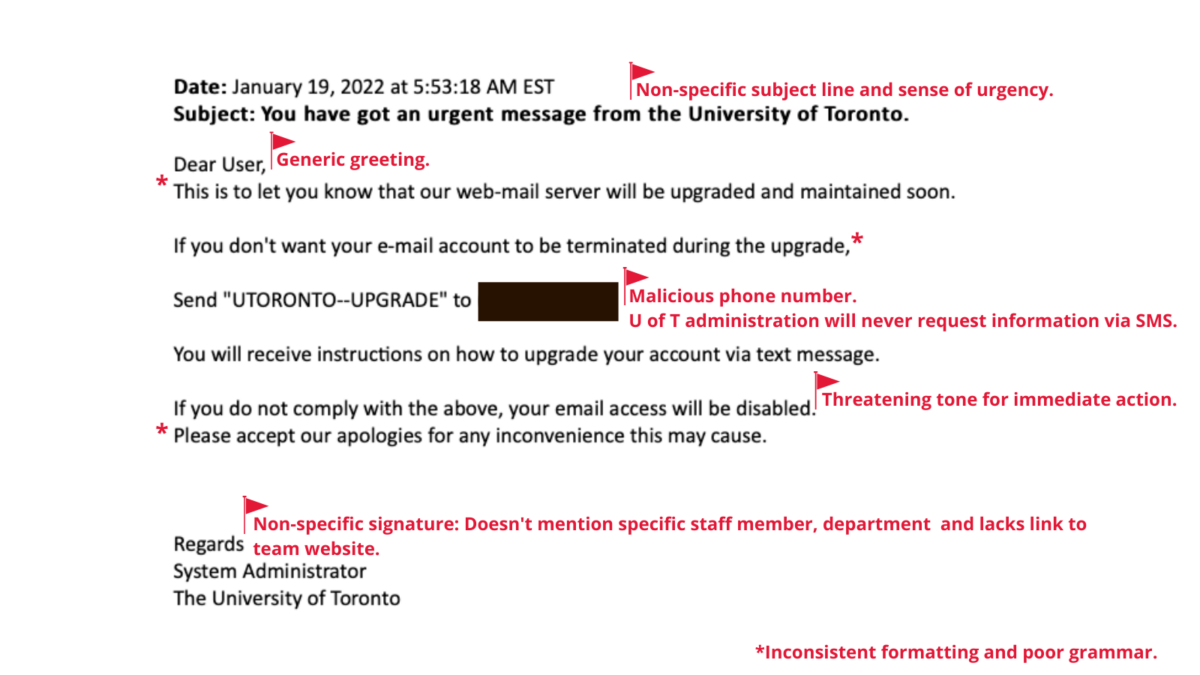
Image 2: This phishing email impersonates a U of T staff member and contains a malicious phone number to respond.
The second email takes a more sophisticated approach as it attempts to get the recipient to respond through a text message. This is called smishing, a type of social engineering where cyber criminals attempt to trick the recipients through text messages. Like phishing, smishing depends on tricking recipients into co-operating by texting or providing personal information.
Spoofing and spear phishing
Email spoofing is a technique hackers use to make phishing emails appear to be from a trusted and legitimate source. For example, the email below (image 4) appears to be sent from Microsoft, however, it includes an urgent prompt to click on a malicious link leading to a spoofed login page. Hackers attempt to mislead recipients into providing their username, password and other important information.
Sometimes, hackers target an individual or a small group within an institution. These emails often address the recipient by name and include personalized language. This is called spear phishing and can be hard to spot without close inspection.
Review the emails below to identify the red flags:
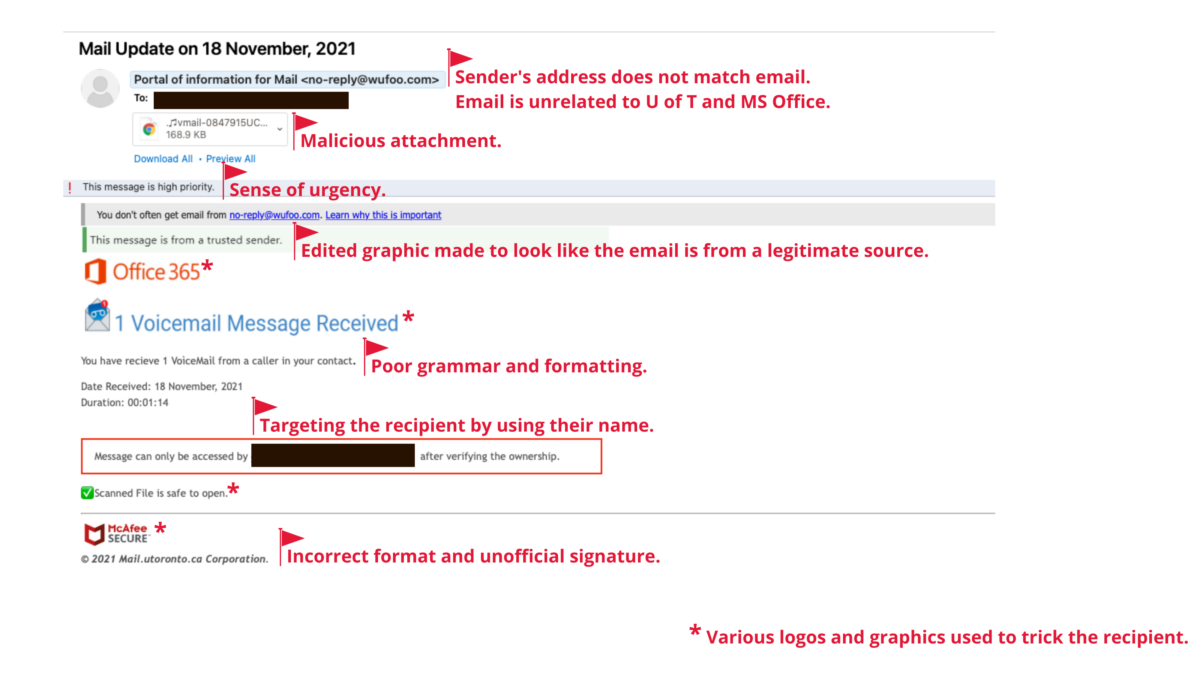
Image 3: This phishing email tries to trick the recipient into thinking they have a voicemail, which is a malicious attachment.
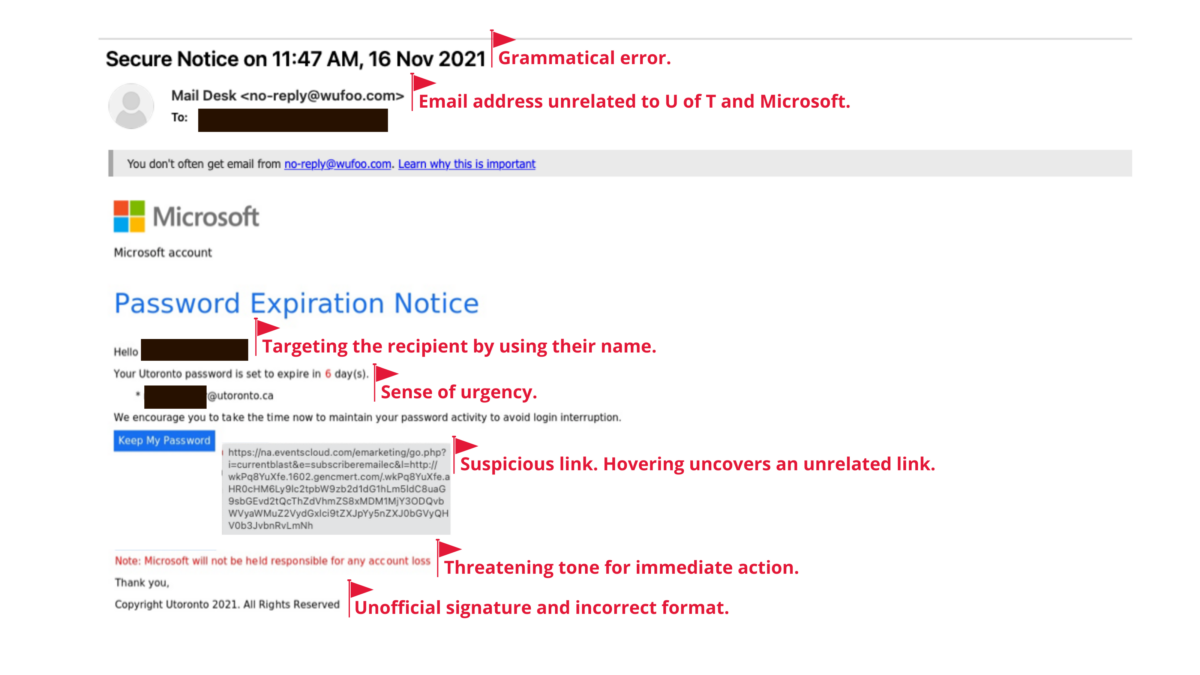
Image 4: This phishing email mimics a system-generated password expiration email from Microsoft and contains a malicious link.
Please note that any information about technology upgrades or updates will always be communicated by your division or department through official U of T communication channels.
Phishing continues to be one of the most prevalent forms of social engineering. For more information about protecting yourself online, please visit https://securitymatters.utoronto.ca/.