In June 2023, the University launched the Security Awareness Training (SAT) Foundations project as part of the broader Security Awareness and Training Program (SATP).
Co-led by Raphaelle Gauriau, Manager, Information Security Strategic Execution, ITS and John Stewart, Information Security Program Manager, I&ITS, U of T Scarborough, the project aims to provide U of T staff, librarians and faculty with baseline training to help improve their knowledge about essential information security topics and threats.
“In an ever-evolving digital landscape, equipping ourselves with the right tools and knowledge is important to keeping our people, data and systems secure and safe. We are hoping the U of T community will join us in this journey to collectively strengthen our digital resilience,” said Raphaelle.
Following the successful launch of phase one, the team is now inviting all tri-campus units to participate in phase two of the project. During this phase, appointed staff from participating units may be onboarded to the project.
Phase two will run from September 2023 to March 2024.
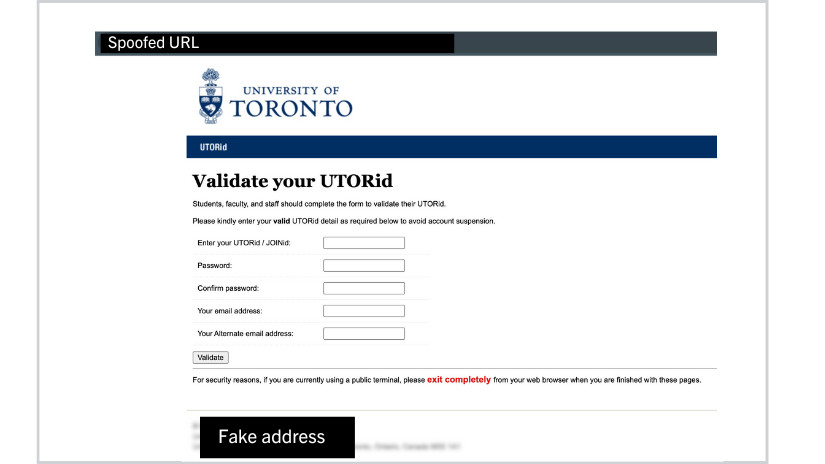
By engaging in phase two, units will have access to comprehensive training modules, thoughtfully designed to be both engaging and informative. These modules cover a wide range of topics, from identifying phishing attempts to safeguarding sensitive data.
The first 20 units to join the program and the first 50 participants to complete the training will have an opportunity to win exciting prizes.
“We are excited to extend the SAT Foundations project to all tri-campus units. Information security is a collective responsibility and by empowering individuals with baseline training, we can collectively build a more secure digital future,” expressed John.
How can units join the project?
Interested units can reach out to Ben Akhirevbulu, Project Manager.
For more information, visit the SAT Foundations web page.