Cyber attacks have increased at an alarming rate with the current geo-political situation being a major contributing factor. The National Cyber Threat Assessment 2020 published by The Centre for Cyber Security suggested a potential increase across Canada in cyber crimes, ransomware and commercial espionage — particularly against businesses, academic institutions and governments to steal intellectual property and proprietary information.
Let’s look back at some interesting information security and ransomware related news in recent months.
Two Canadian Universities hit by cyber attacks
Simon Fraser University and Lakehead University reported that they were hit by cyber attacks in February. Although the universities did not confirm whether it was a ransomware attack, they advised students and staff to monitor their accounts, change their passwords and enrol in multi-factor authentication (MFA).
Data breaches can result in the loss of personal, institutional and other sensitive information. Learn how to enrol in MFA to add an additional layer of security to your online accounts.
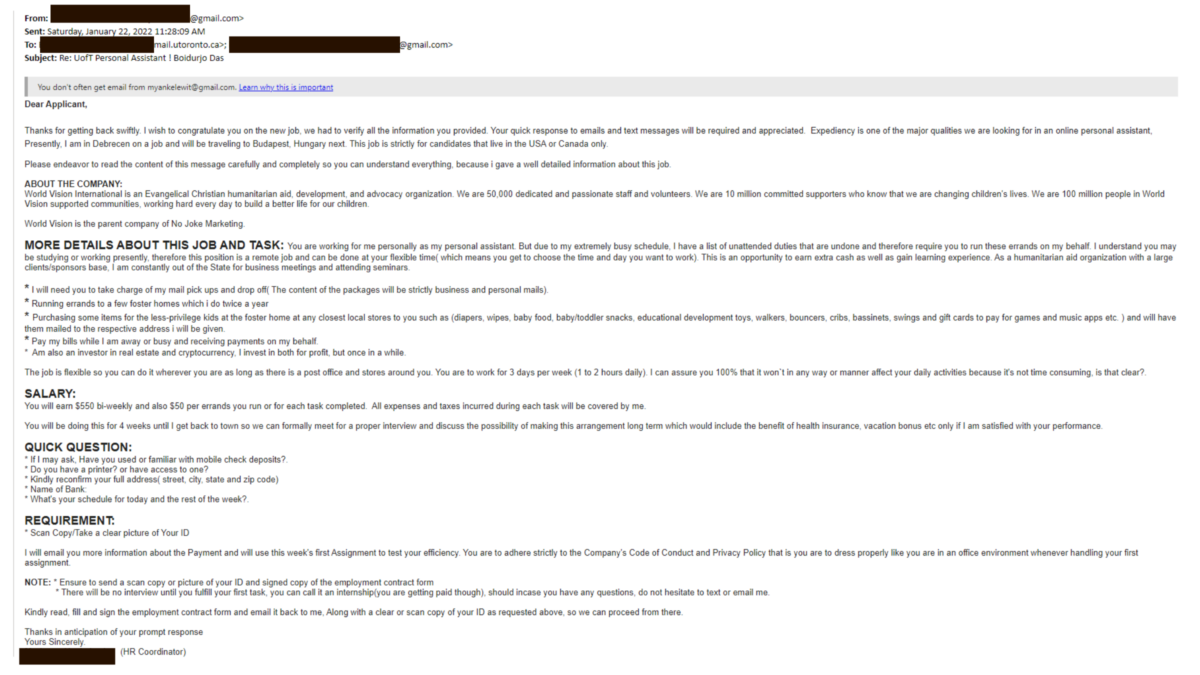
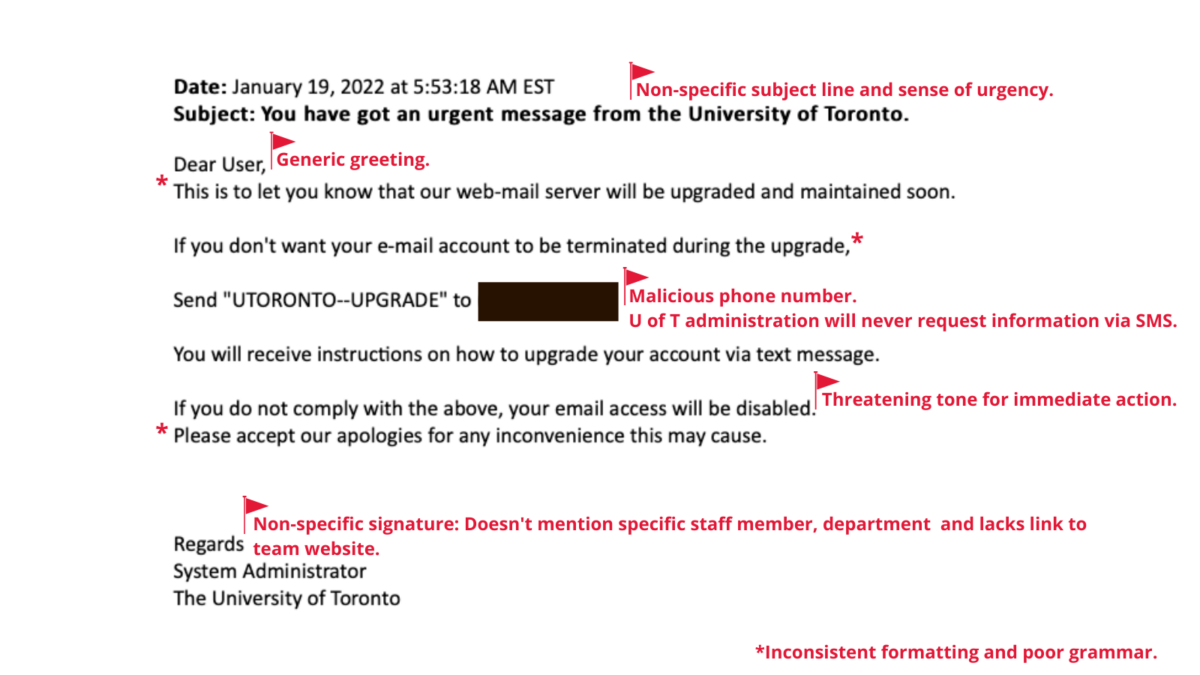
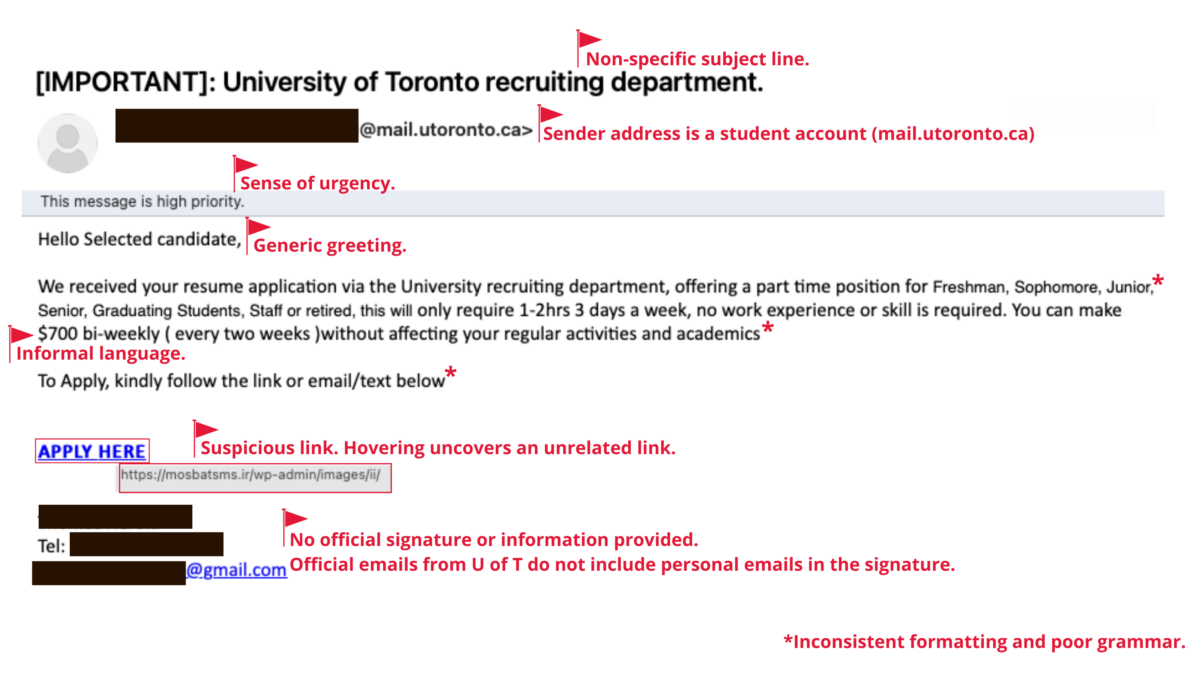
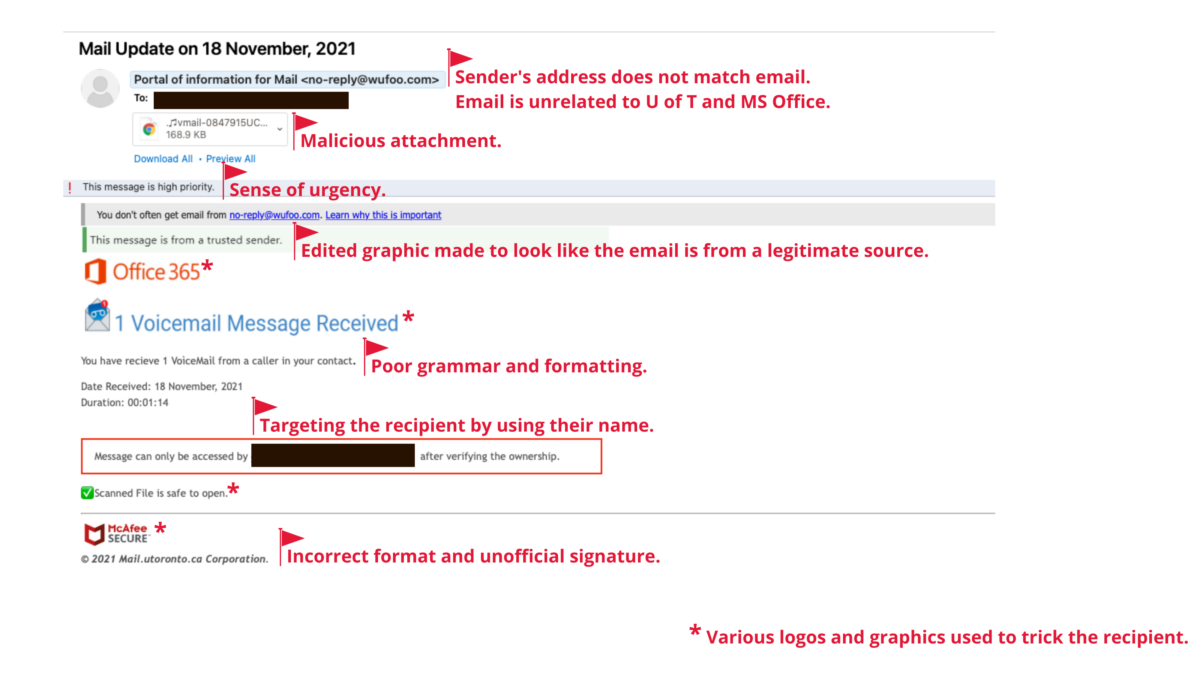
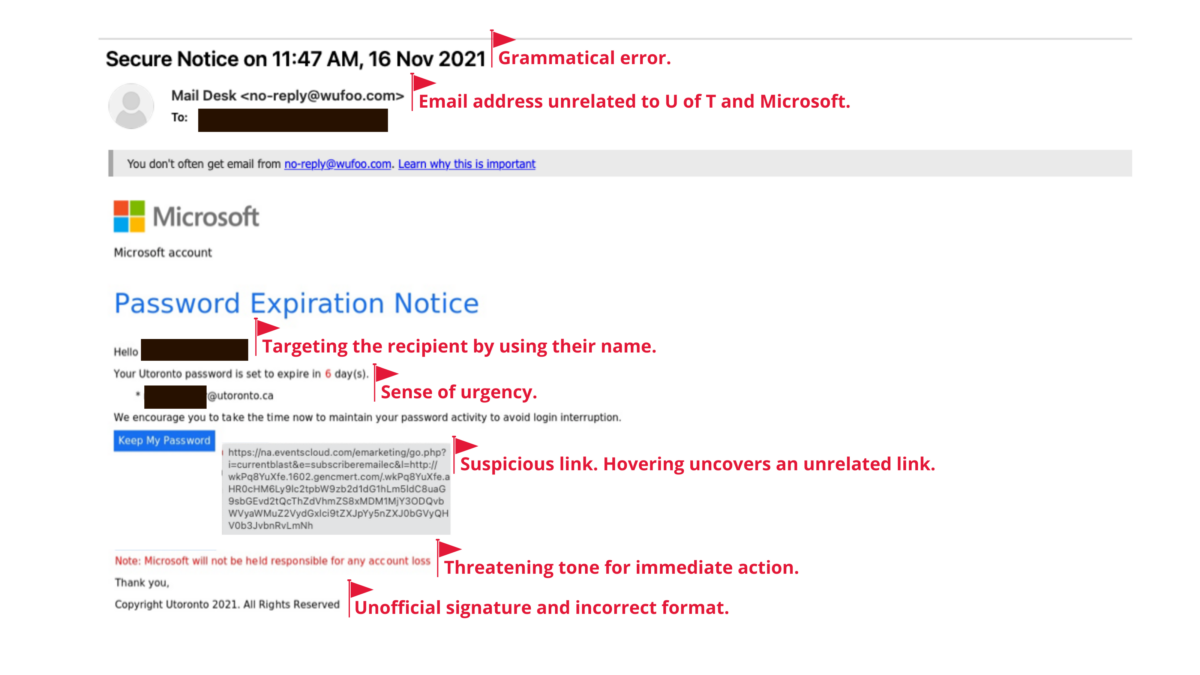
Hackers getting clever with phishing emails
It is often said that hackers stay one step ahead of you by constantly changing their tactics. In a recent blog post by Mount Royal University, it was reported that phishing emails with fake invoices from MasterClass (an online educational platform) were sent to the university community and hackers asked recipients to respond with their credit card information for a refund.
Often, phishing emails are made to look like they are from a legitimate source, which can lead recipients to respond, causing further damage. Check out the Phish Bowl for examples of phishing emails received by members of the University of Toronto (U of T) community to help you identify and report suspicious emails.
Ransomware attacks increasing at an alarming rate in Canada
A recent article published by MaRS explained how ransomware attacks have been increasing in Canada with small businesses losing up to billions to cyber attacks. In fact, a survey done by Canadian Internet Registration Authority (CIRA) also found that nearly 70 per cent of Canadian organizations that experienced ransomware paid the hackers to regain access to their data.
Last year, U of T launched a ransomware awareness campaign called Expect Ransomware to provide the community with resources, tips and tools to protect their accounts and to stay secure online.
Federal government may make reporting cyber attacks mandatory
Public Safety Minister Marco Mendicino has said that the federal government might make it mandatory for Canadian businesses and organizations to report cyber attacks. Mendicino also emphasized that the current geo-political situation has increased the threat of cyber attacks.
Staying safe and secure online can be done through simple but effective steps. Explore the educational resources on the Security Matters website to learn how to stay secure online.