The University of Toronto’s (U of T) Information Security Incident Response Plan is available to help information technology (IT) managers, non-IT unit leaders and other employees handle security incidents effectively.
We interviewed three Information Security directors to ask what we need to know about the plan and how it can help you deal with security incidents. Responses come from Deyves Fonseca, Associate Director, Information Security Operations, Kalyani Khati, Associate Director, Information Security Strategic Initiatives and Alex Tichine, Director, Information Technology, Faculty of Applied Science & Engineering.
This interview has been edited for length and clarity.
Why was the Information Security Incident Response Plan created?
Deyves: The plan is meant to help guide the University in dealing with and responding to security incidents. It’s an index including guidance, approaches and procedures that employees can follow when they experience security incidents. The fact is that security incidents happen on an ongoing basis and there is no 100 per cent protection against them. In addition to protecting against security incidents, we need to have plans in place to ensure that employees know how to deal with security incidents in the best way possible.
Alex: The Incident Response Plan was created to provide a consistent approach to dealing with information security incidents, so that everyone who has a role to play in dealing with these incidents knows what they need to do and can act quickly. When a security incident happens, there are many questions that come up about how to determine the severity of the incident, who to contact, how to communicate about the incident, what resources are available, etc. The plan helps to bring all these components together.
What do you want employees to know about handling security incidents?
Kalyani: Preparation is key and that includes reviewing and testing the Incident Response Plan before an incident occurs. When an incident is underway, that is not the time to test the plan for the first time. Not knowing what to do next and who to contact can slow down response and worsen the situation. It is critical that teams involved in incident response have a clear understanding of their roles and responsibilities and have practised their response.
Deyves: I encourage employees to spend some time getting to know the plan so that they can respond to security incidents quickly and effectively. One of the key phases of the incident response process is called ‘preparation’, which will help employees understand how to respond to incidents quickly. Being prepared will help you to bring your unit back to business as quickly as possible in the event of an incident.
Alex: Don’t panic! Use the Security Incident Response Guide to work through the incident. To make sure you are prepared for when an incident happens, the most important thing is for divisions to review and test the plan on a regular basis. Divisions can then fine-tune the plan to suit the needs of their division.
Any tips on how employees can practice what to do in the event of a security incident?
Kalyani: One great way to practice your response is by conducting tabletop exercises. These exercises not only help teams validate their response plans, but also ensure that individuals understand their role in the event of an actual incident. When conducting tabletop exercises, select scenarios that are realistic and resonate with the participants. We have sample scenarios available for units to run their own tabletop exercises.
Deyves: Tabletop exercises can make handling live incidents easier. When you do a simulation, you see what works and what doesn’t work, what you understand and what you don’t, and what you might be missing so that you can effectively respond to incidents when the time comes.
Alex: As an example of a tabletop exercise, you might go through a scenario where you learn that your unit’s official social media accounts have been compromised, and someone is sending out notifications through your social media to students and alumni claiming that your unit has been compromised. You would then determine that multi-factor authentication (MFA) could be enabled on social media accounts to enhance security. This is how the tabletop exercise can help you identify immediate opportunities to enhance your level of security.
How can people protect themselves from security incidents?
Kalyani: Self-enrol in UTORMFA, U of T’s MFA solution, and use MFA on your personal accounts such as bank accounts or other critical accounts. Enable MFA wherever you can!
Deyves: The most common incidents we see include account comprise, device compromise and phishing events that can potentially lead to security incidents. MFA is the single-most effective tool you can use to protect against account comprises and ransomware. Employees can also refer to the guidance we have on protecting from ransomware, particularly during remote work.
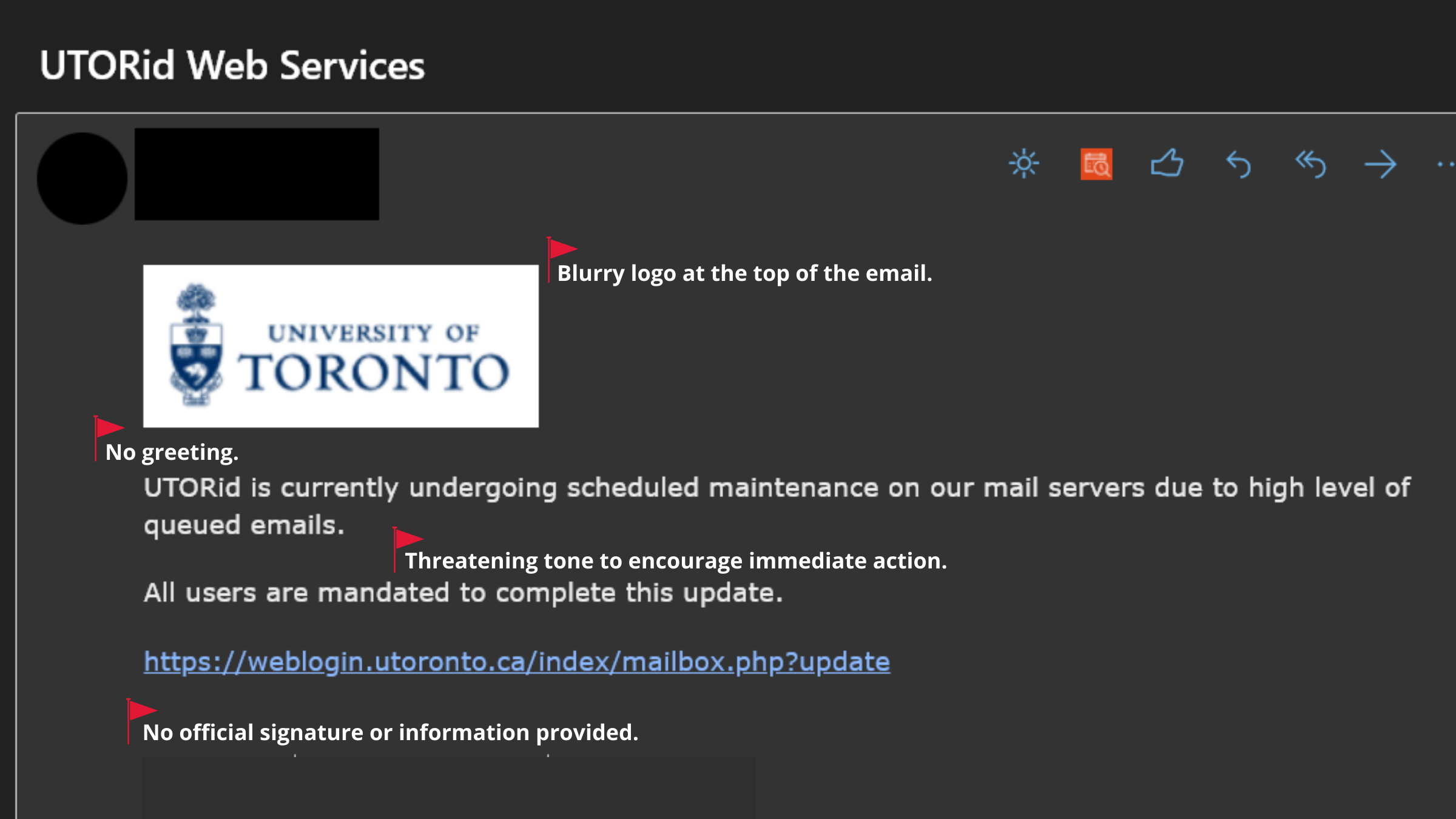
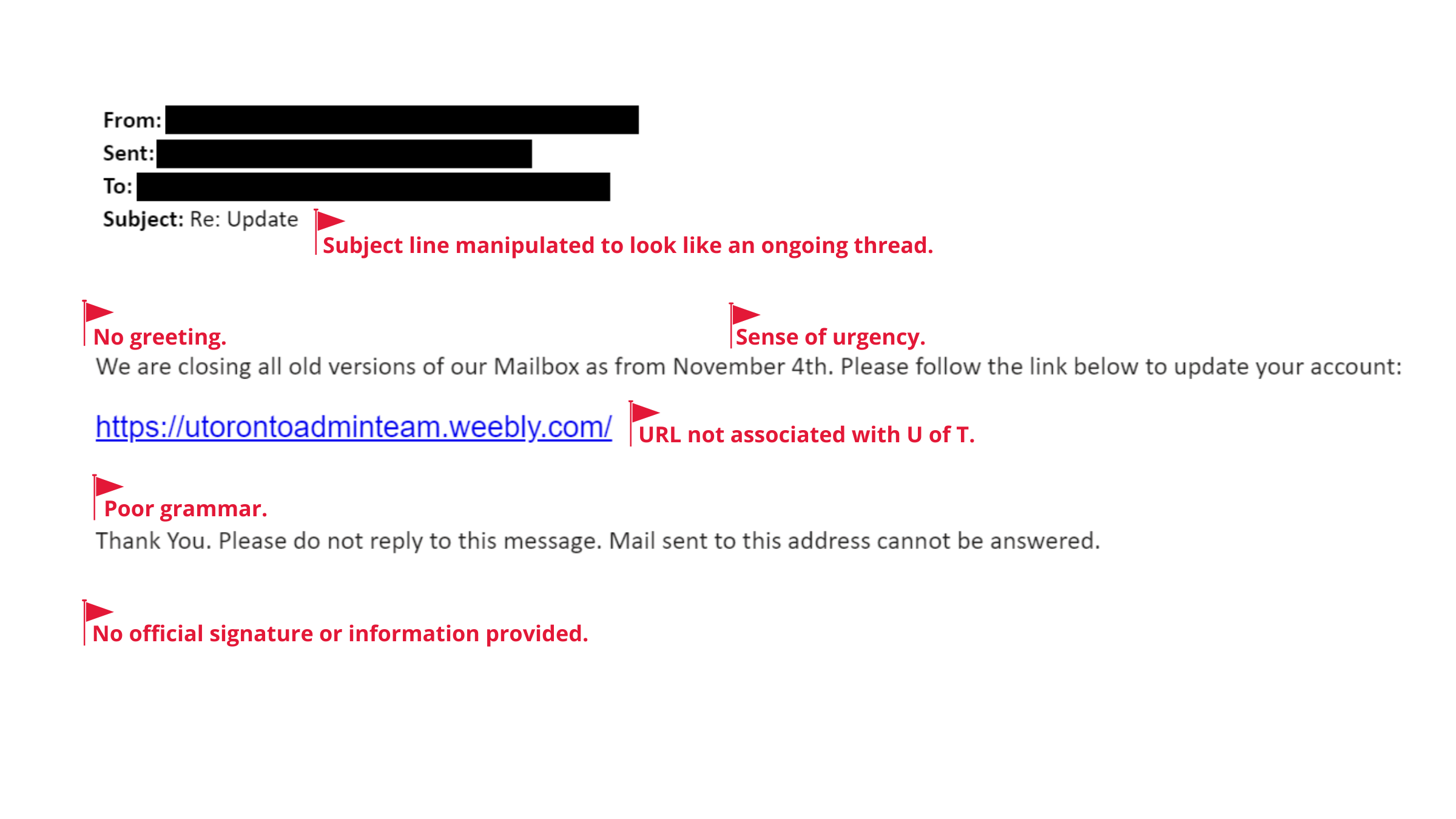
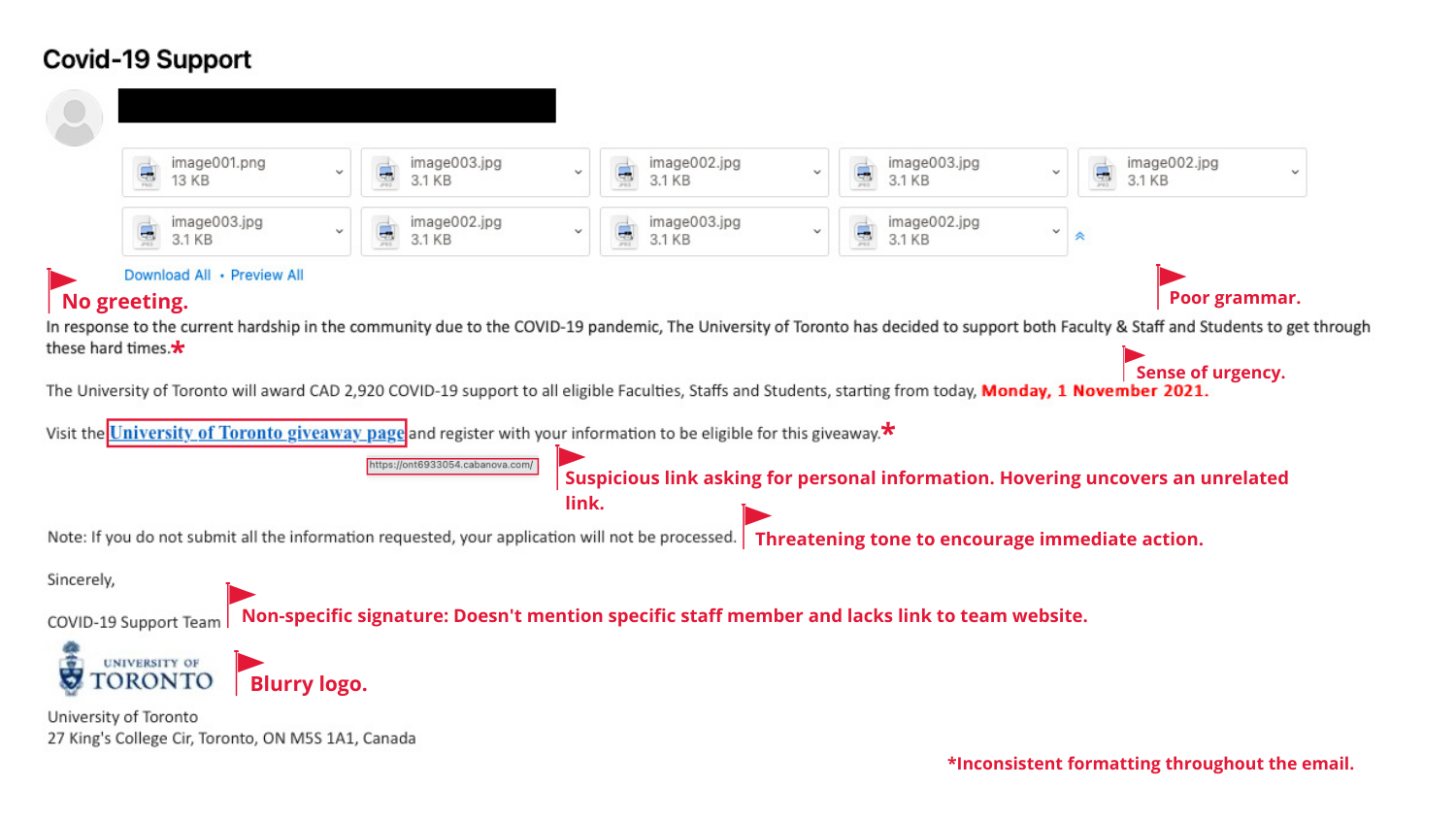
Alex: Patching is so important to help minimize incidents. Another tip is to be vigilant when it comes to phishing and social engineering attacks. Just when you think you’ve figured out what phishing looks like, there is something else around the corner that you may not have seen before.
Deyves: In terms of data protection and privacy, know what you’re consenting to when you provide your data. The more that you share your data, the more you expose yourself to comprises because companies who hold your data are subject to data breaches.
Do you have questions about how to handle security incidents? Contact security.reponse@utoronto.ca.