The battle against phishing attacks is an ongoing, daily task. Though we are equipped with highly-sophisticated and advanced tools for protection, hackers retaliate by evolving their techniques to evade these protections.
It is important to continually educate ourselves and maintain awareness about phishing attacks to ensure our individual and institutional data remains protected. Hackers use techniques such as spear phishing to persuade email recipients to click a link which can then distribute malware onto their devices or grant hackers access to their data. Some phishing attacks are used as means to steal credentials, which can cause further damage to both the recipient and the University of Toronto (U of T) on a higher level.
Since the beginning of the COVID-19 pandemic, Statistics Canada has determined that just over four in ten Canadians have received a phishing attack. Hackers have been taking advantage of people’s vulnerable state in these unprecedented times by sending fraudulent emails that attempt to trick recipients into revealing personal information or clicking on malicious links or attachments.
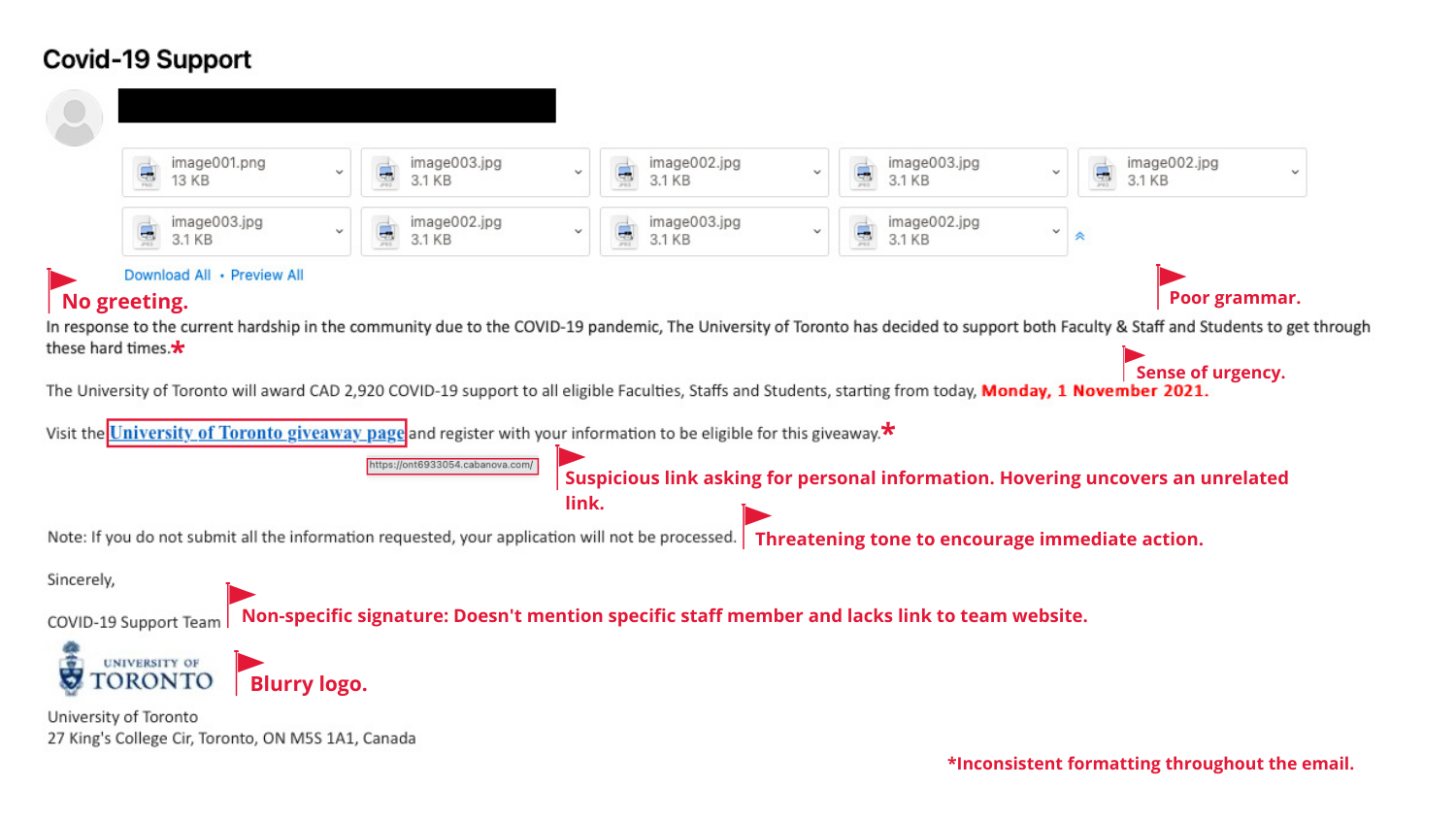
On Nov. 1, 40,000 U of T community members received an email from the University’s ‘COVID-19 Support Team’ (which does not actually exist). This email encouraged recipients to fill out a form on the ‘University of Toronto giveaway page’ to become eligible for a one-time cash reward.
If you received this email, please ensure to report and delete the email immediately.
Take a look at some of the red flags to help you identify a phishing email:
- No greeting: Phishing emails are usually sent in mass, and therefore rarely include a personalized greeting. Instead, it’s common to see a vague greeting such as “Dear Member”, “Hello” or no greeting at all.
- Poorly written email: One of the more common signs of a phishing email is spelling mistakes and poor grammar. Another sign is formatting inconsistencies throughout the email. Notice how the font size, type and colour changes in this example.
- Suspicious link: Phishing emails almost always contain a link that either takes users to a cloned website or downloads malicious software. These links are often crafted to appear genuine by using a URL that looks like a legitimate one. One of the ways to verify a URL’s legitimacy without clicking on it is by hovering your cursor over the link and verifying the address revealed in the popup box. In this email, hovering over the link revealed a link that is not associated with U of T.
- Threat and a sense of urgency: Emails that threaten negative consequences should always be treated with caution. This is a tactic used by hackers to encourage or even demand immediate action, which flusters the recipient into acting without being given time to think about it. Note how the hacker threatened the recipient into providing their personal information in order for their application to be processed.
What to do if you receive this phishing email:
- Do not act on any of the email prompts including clicking the link, providing personal information or opening the attachment.
- Forward it to report.phishing@utoronto.ca and then delete it from your inbox.
- If you already clicked on the link or attachment, please contact security.response@utoronto.ca immediately for assistance.
- To help prevent future phishing attempts, we encourage community members to enrol in U of T’s multi-factor authentication (MFA) service, UTORMFA: isea.utoronto.ca/services/utormfa/self-enrollment/.
For more information about protecting yourself online, please visit: https://securitymatters.utoronto.ca/.