Data breaches and ransomware have become massive risks costing large losses to both individuals and organizations around the world. IBM reported that 2021 saw the highest average cost of a data breach in the last 17 years, with the cost rising from $3.86 million to $4.24 million USD on an annual basis.
As we prepare to recognize Data Privacy Day on Jan. 28 and raise awareness about safeguarding our personal information, let’s take a look at five data breaches that made headlines in 2021 and learn how to keep ourselves safe online:
Data of more than 500 million Facebook (Meta) users leaked online
Personal information (full names, phone numbers, locations, birth dates and more) of 533 million Facebook (Meta) users was leaked online and made available for free on a hacking forum in April 2021. The data exposed include data of users from 106 countries, including over 32 million records on users in the U.S., 11 million on users in the UK, and 6 million on users in India.
Review these information security tips to learn how to protect yourself online.
Ransomware attack against Superior Plus
In December 2021, Canadian propane distributor Superior Plus reported a ransomware attack which disrupted the company’s computer systems. The company said that theyhad to temporarily disable certain computer systems and applications while they investigated the incident.
Ransomware attacks can lead to long-term and significant damage—from loss of sensitive data to shutting down operations. Learn how you can protect yourself from ransomware.
Luxury retailer Neiman Marcus data breach impacts over 4 million customers
In September 2021, American luxury retailer Neiman Marcus reported a data breach that impacted 4.6 million customers. Though the leak took place in May 2020, it was only detected in September 2021. The leak also included the potential theft of over 3.1 million payment cards belonging to customers.
Check out this blog post to learn how to stay safe while shopping online.
Hackers access personal details of 4.5 million Air India passengers
In March 2021, India’s national airline Air India reported a cyber-attack on its data servers, which affected about 4.5 million customers around the world. The information leaked contained various forms of personal information. The airline claimed that no passwords were stolen but asked its customers to immediately change their Air India password for protection.
Strong passwords are the first line of defense in protecting your institutional data and personal information. Learn more about the importance of safe password practices.
Canada Revenue Agency (CRA) locks out taxpayer accounts after discovering use of unauthorized credentials
Last year, taxpayers were locked out of their CRA accounts for about 800,000 accounts. The CRA claimed that the credentials may have been obtained through email phishing or third-party data breaches.
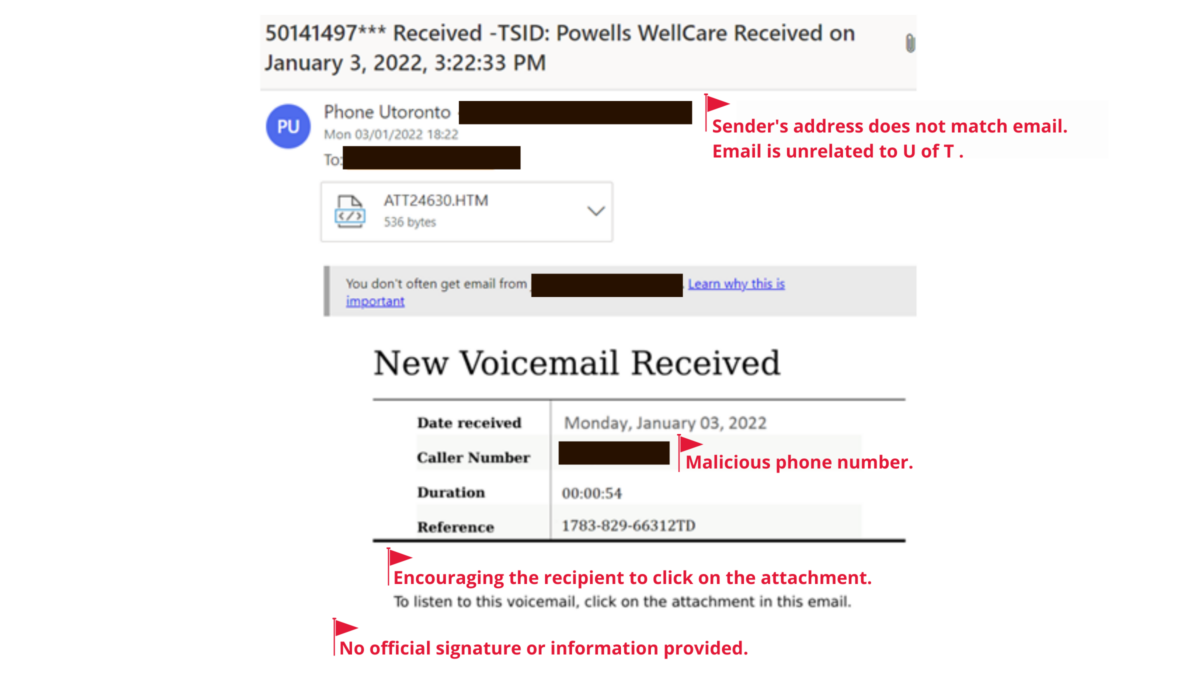
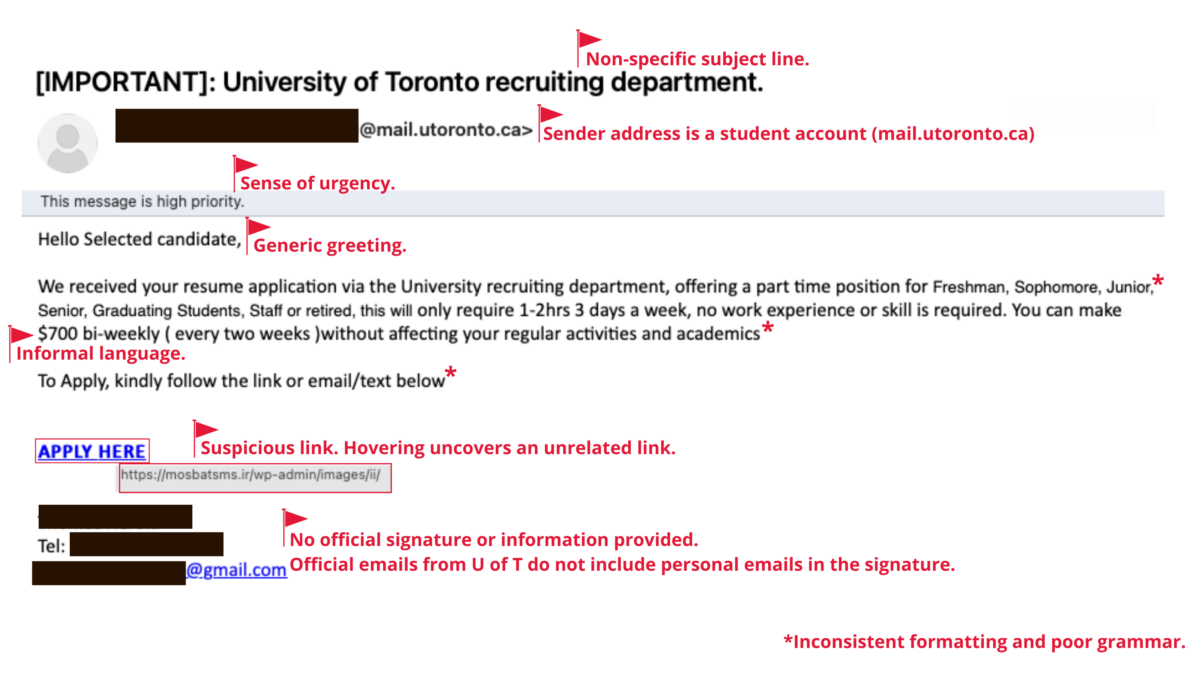
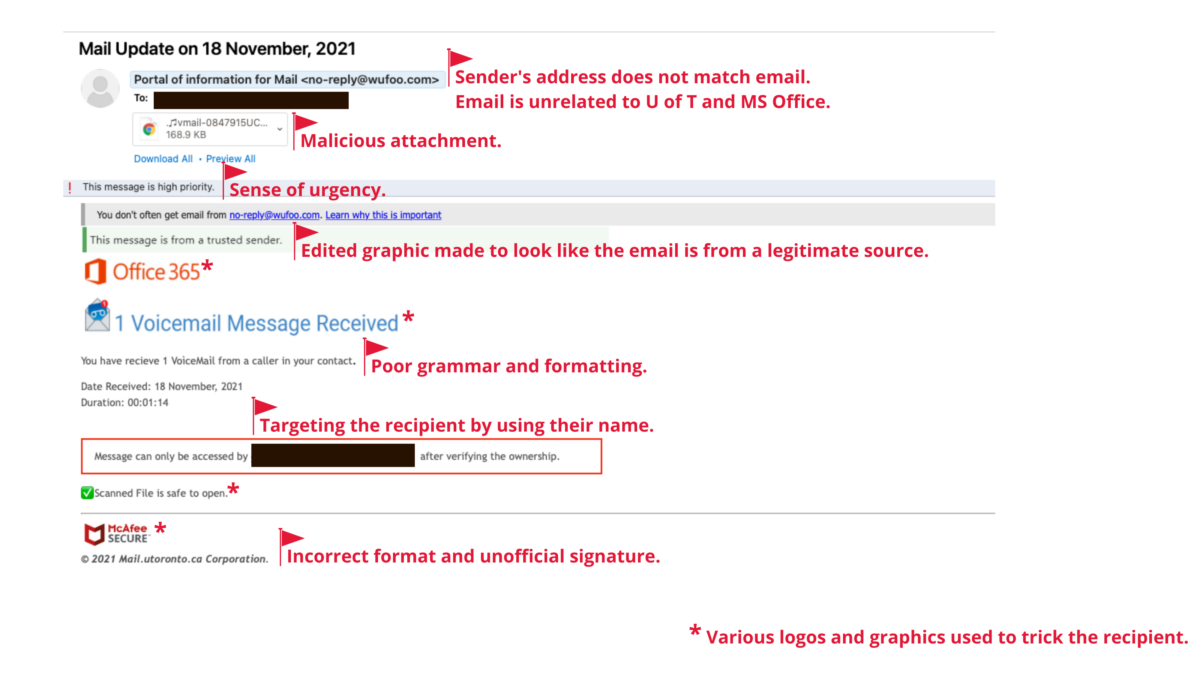
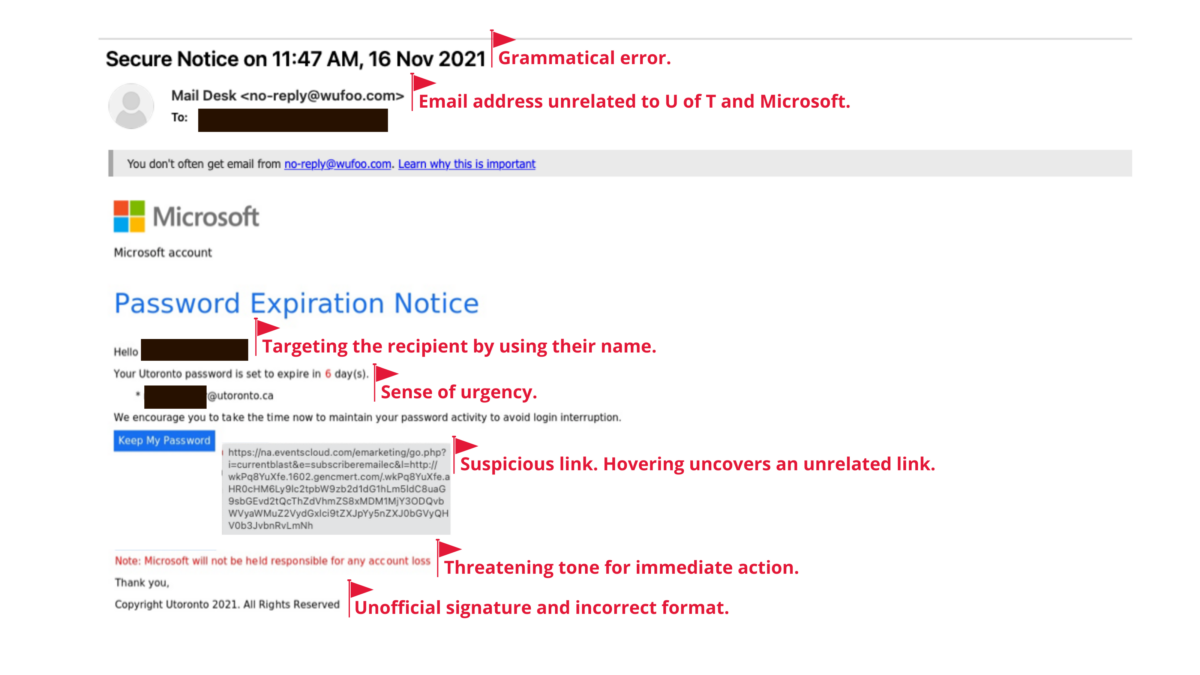
In today’s age, it is of utmost importance to stay alert and protect ourselves from phishing attacks. Learn how to identify and report phishing attacks.