To celebrate Data Privacy Day on Jan. 28, Information Technology Services (ITS) hosted a virtual panel event: Impact of evolving technology and privacy laws in higher education. The one-hour event opened a conversation about data privacy and protection and answered privacy questions from the University of Toronto (U of T) community.
Over 145 attendees including staff, faculty and students from the tri-campus community joined virtually to learn from legal, cybersecurity and privacy experts on how changes in technology and privacy laws impact higher education. The featured panelists were:
- Ashley Langille, Information Privacy Analyst
- Carlos Chalico, IT Risk and Privacy Consultant, EY & Instructor, School of Continuing Studies, U of T
- Daniel Michaluk, Information Security and Privacy Lawyer & Partner, Borden Ladner Gervais LLP
- Deyves Fonseca, Associate Director, Information Security Operations
The event was moderated by Rafael Eskenazi, Director, Freedom of Information and Protection of Privacy (FIPP) Office.
“The Data Privacy Day virtual panel event provided a great opportunity to engage with the U of T community, to answer their questions about privacy and to share University resources they can use to protect personal information,” said Kalyani Khati, Associate Director, Information Security Strategic Initiatives.
Highlights from the event
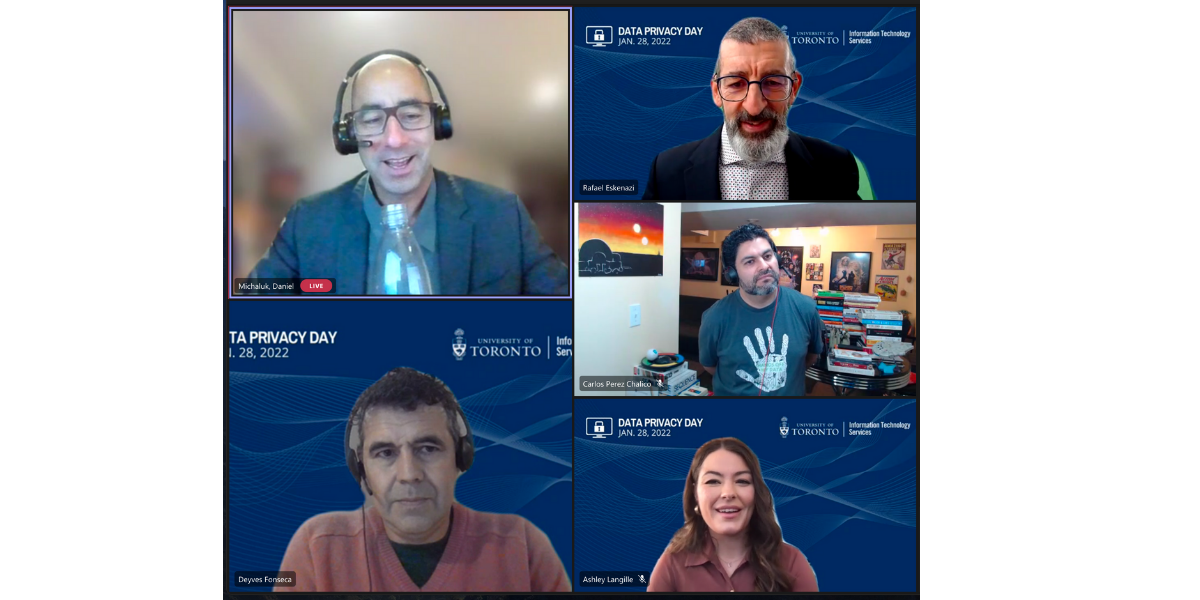
From left to right: Deyves Fonseca (bottom left), Daniel Michaluk (top left), Rafael Eskenazi (top right), Carlos Chalico, Ashley Langille (bottom right)
Daniel Michaluk began the session by speaking about the Freedom of Information and Protection of Privacy Act (FIPPA) and observed how there hasn’t been an adverse regulatory finding about a university’s privacy practices since FIPPA was introduced in Ontario. Michaluk explained that this can be attributed to the good work done by the universities of Ontario, so there is no historical basis for additional regulation in the sector.
“Right from the start in 2006, all the Ontario universities took FIPPA and privacy protection very seriously, and from some good work early on by the Council of Ontario Universities, there’s been a continuous dialogue in the sector about privacy,” he said.
Speaking about the University’s digital transformation, Deyves Fonseca expressed that the pandemic brought significant changes with the move of data to the cloud. He said that the move to using the cloud is going to continue and accelerate as part of U of T’s digital transformation as we prepare to go back to in-person work and learning.
Collaboration was the keyword during Carlos Chalico’s presentation. “We need to think about collaboration across organizations to minimize cyber security risks,” said Chalico. “Alliances are necessary within organizations to protect information as a business issue, not just a tech issue.”
Ashley Langille remarked that the inclusion of stricter General Data Protection Regulation (GDPR) focused language in privacy policies has created issues with informed consent, as the language in these policies often only apply to data of European Union (EU) citizens and is often misinterpreted to apply to all users. Ashley noted that inclusion of a GDPR protection in policy does not necessarily translate to FIPPA compliance.
The presentations were followed by a Q&A session which consisted of pre-submitted and live questions from the audience. Some key highlights from the Q&A session:
Raffle winners
Two attendees were randomly selected to win a $50 U of T Bookstore gift card. Congratulations to the raffle winners:
- Bismah Khalid, On Location Accessibility Advisor, University of Toronto Accessibility Services
- Linda Ye, Senior Auditor – Information Systems, Internal Audit Department
Visit the Security Matters website to learn more about protecting yourself online and your data.