Though most of the world is beginning to feel an end to the harsh effects of the COVID-19 pandemic, the cyber security world is still seeing an increase in vulnerabilities because of the shift in remote network dependencies. As a result, cyber security attacks continue to be a hot topic in local, national and international news coverage. Here is a brief roundup of some of the most interesting recent news items from the past few months.
The United States’ largest gasoline pipeline was shut down on May 7 due to a ransomware attack by suspected Eastern European-based criminal gang DarkSide. As a result of some of its business network systems being affected, Colonial Pipeline said it notified law enforcement and temporarily shut down its operations to contain the threat. In response to this attack and a series of intrusions by other overseas hackers, the U.S. federal government is issuing new cyber security regulations.
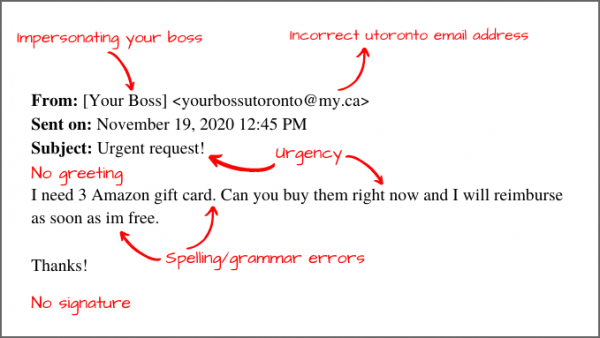
Insight: Although DarkSide claims they do not attack schools or non-profit organizations — only big organizations that can afford to pay large ransoms — the University of Toronto (U of T) is taking steps to ensure its community and their data is protected.
On May 30, global meat packing giant JBS was forced to shut down some of the world’s largest slaughterhouses due to a ransomware attack affecting its servers. JBS suspects a criminal organization in Russia was the source of the attack. According to White House Deputy Press Secretary, Karine Jean-Pierre, the White House is assisting JBS in their efforts to mitigate the threat.
Insight: Ransomware attempts targeting the food and commodities industries have become a trend since May 2020. Following the Colonial Pipeline attack, the attack on JBS also occurred “as the meat industry battles lingering COVID-19 absenteeism” because of plants being shut down last year.
On June 14, Humber River Hospital officials shut down the information technology systems after discovering a ransomware attack which was attempting to corrupt patient health records. While no confidential information was released due to a quick response, the shutdown impacted patient care, including prolonged wait times.
Insight: Christopher Parsons, Senior Research Associate at Citizen Lab, said, “Humber River Hospital appears to have had appropriate safeguards in place and enacted a quick and accurate response to the ransomware attack.”
In January 2021, a security researcher discovered and privately disclosed that there was a privacy flaw in Peloton’s Application Programming Interface (API). This flaw allowed anyone to view Peloton users’ personal details including age, gender, city, weight and workout statistics. Though Peloton was slow to respond, the vulnerability was fixed months later in May 2021.
Insight: In response to this specific leaky API, Setu Kulkarni, the Vice President of Strategy at WhiteHat Security said: “while APIs promise agility, personalization and connectivity between services, they are also becoming the most vulnerable point of attack.” For developers, Kulkarni recommends taking the following two steps:
- Test your APIs in production for application security vulnerabilities and mitigate those vulnerabilities using API management solutions in production.
- Start adding security-based exit criteria for APIs in development.
In April 2021, it was revealed that a cyber espionage campaign was targeting organizations that use Pulse Connect Secure networking devices. However, newly uncovered details confirm that many high-value and well-protected entities, including Verizon and the New York subway system, were among those targeted. It is unclear if any sensitive information was compromised, but the hackers’ access to these systems is still worrisome.
Insight: Although the Chinese government has not been officially blamed for these attacks, U.S. President Joe Biden has put priority on monitoring China’s rising influence, as it is speculated that these attacks may be a tactic in China’s race to advance its economy.
What is the University of Toronto (U of T) doing to help protect its community from such threats?
For more tips on staying safe online, visit the Remote Security Matters webpage.