Phishing has become one of the most popular subsets of social engineering. It is likely that most people have received an email urging action on an unknown link or attachment to prevent being ‘locked out of your accounts’. According to the 2021 Data breach Investigations Report (DBIR) by Verizon, 36 per cent of online breaches involved phishing, which is an 11 per cent increase from last year.
While some phishing emails might look suspicious due to poor grammar, spelling mistakes and other red flags, hackers have become more advanced, and their phishing attempts are more successful. Spear phishing is one of the most common and dangerous methods used to conduct fraud, usually on specific individuals or organizations. Often, the recipients are asked to open a malicious attachment or click on a link that takes them to a spoofed website where they are asked to provide passwords or other personal information.
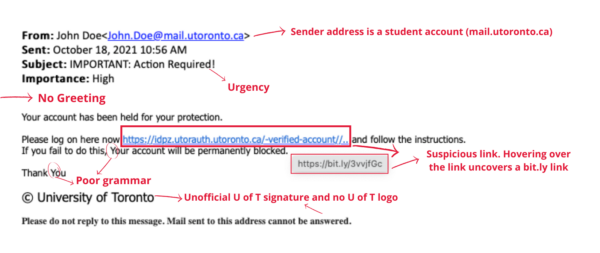
Recently, members of the University of Toronto (U of T) community received a phishing email that contained a link leading to a spoofed version of the UTORid login page. Here are some of the red flags that were present in the email:
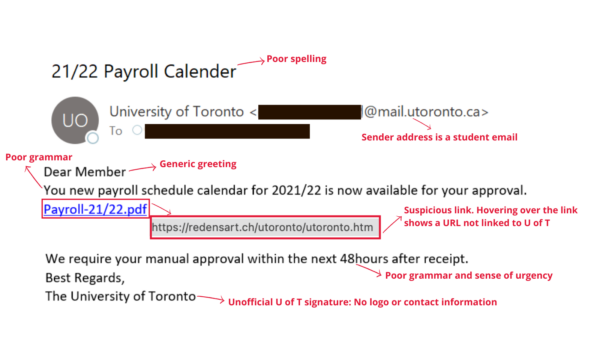
- Email spoofing: Email spoofing is the act of sending phishing emails from a forged email address. This is a technique used in most phishing emails to get the recipients to open and engage with the email. In this instance, the hacker is attempting to impersonate U of T administration by using an official U of T email domain.
- Generic greeting: Legitimate emails from a trusted organization or emails exchanged between colleagues will often include a direct greeting (your name). Hackers typically use generic greetings such as “Dear Member” or “Good morning” because they are sending mass emails and do not have access to your personal information (name). However, more advanced attacks may address you by name, which is why you should stay informed of all the different phishing red flags.
- Suspicious link and cloned web page: This phishing email contained a link to a .PDF extension — hovering over the link uncovered a suspicious URL unrelated to any known U of T websites. This link leads to a cloned version of the UTORid login page. A cloned webpage works by copying the front-end of a website to trick the email recipient into trusting the page and inputting their personal information. U of T staff, faculty and students will never be asked to provide their UTORid credentials via email.
- Poorly worded email: Often, you can spot a phishing email by the poor use of grammar and spelling. Right from the subject line, this email displayed both these flaws. Always ensure to read the email carefully and check for spelling and grammatical mistakes, as well as oddly worded sentences.
- Demanding urgent action: A common tactic used by hackers is to create a sense of urgency. This tactic is widely successful because recipients feel too rushed to analyze the email in detail and are more likely to fall for the attack. In this instance, the sender asked the recipient to manually approve the schedule within “48hours” (note the grammatical error) of receiving the email.
Learn more about identifying and reporting a phishing attempt.