The Information Security Council (ISC) exists to ensure broad consultation in planning and decision-making processes as it relates to information security. Officially formed in February 2018, its creation stems from the Policy on Information Security and the Protection of Digital Assets and the recommendations from the Working Group on the Implementation of Information Risk Management Practice.
New web page offers security resources for remote workers
Making the transition into remote working can be overwhelming as we all try to adjust to our new environments and routines. To ensure cyber safety isn’t compromised during this time of uncertainty and isolation, the Information Security team is regularly updating the Security Matters website with up-to-date tips, videos and resources.
The new Remote Security Matters web page explores a variety of topics, including:
- Protecting your home network
- Identifying and reacting to personalized attacks
- Safe password practices
- Protecting yourself and your device against malware
For more information, visit Remote Security Matters.
Review this site often as new information will be posted and shared regularly.
Protect your network
Almost every home network starts with a wireless (often called Wi-Fi) network. This means securing your wireless network is a key part of protecting your home. We recommend the following steps to secure it:
- Change the default administrator password on the device controlling your wireless network. The administrator account is what allows you to configure the settings for your wireless network.
- Ensure that only people you trust can connect to your wireless network. Do this by enabling strong security including requiring a password for people to connect to your wireless network. Once connected, their online activities are then encrypted.
- Make sure the password you provide to people using your wireless network is a strong password that is different from both the administrator password and the network name.
- Remember you only need to enter the administrative password once for each of your devices, as they store and remember the password.
Not sure how to perform these steps? Ask your Internet service provider, check their website, check the documentation that came with your wireless access point, refer to the vendor’s website, review the first 80 seconds of this video:
Other tips to protect your home are:
- Know and secure other network devices in your home
- Keep your home systems up to date
- Use two-step verification for your online accounts
- Back-up your data
Details are also shown in the fact sheet on “Creating a Cyber Secure Home.”

Protect your passwords
When a site prompts you to create a password: create a strong one — the more characters it has, the stronger it is. Using a passphrase is one of the simplest ways to ensure your password is strong. A passphrase is a password made up of multiple words such as “beehoneybourbon.” We recommend you also use a unique passphrase for each device or online account. This way, if one passphrase is compromised, all of your other accounts and devices are still safe.
Can’t remember all your passphrases? Use a password manager, which is a specialised program that securely stores all your passphrases in an encrypted format (and has lots of other great features too!).
Finally, enable two-step verification (also called two-factor or multi-factor authentication) whenever possible. It uses your password, but also adds a second step, such as a code sent to your smartphone or an app that generates the code for you. Two-step verification is probably the most important step you can take to protect your online accounts and it’s much easier than you may think.
See more detail in this document.

Additional Security Matters articles about passwords:
Tax filers beware: CRA impersonators attack through phishing emails
Tax season is upon us and cyber criminals are using this opportunity to set traps for taxpayers. A common scam is phishing emails that purport to be official communications from tax filing companies or legitimate messages from the Canada Revenue Agency (CRA). They often contain deceptive language that entices the recipient(s) to follow specific instructions.
Common types of scams
The CRA has identified some known types of tax-related scams, including but not limited to:
- Messages that encourage you to click on a link to claim a refund.
- Messages that notify you of an unpaid balance and threaten you with jail time if you don’t pay.
- Messages that instruct you to follow a link to review changes in your account or to fill out a form with your login credentials and personal information.
Tax refund phishing email received by members of the University of Toronto (U of T) community:
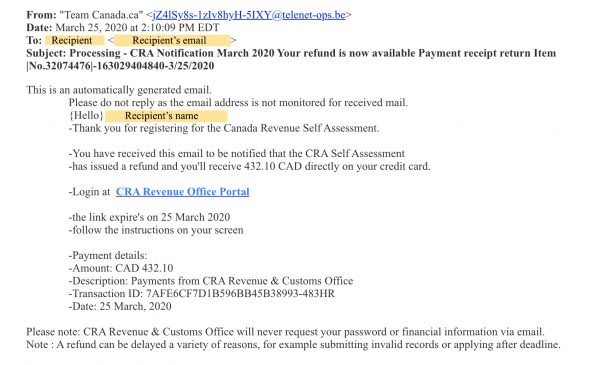
Resources on what the CRA does and does not do when they contact you. The CRA also provides examples of fraudulent emails.
What to do if you suspect a phish
If you received a suspicious email relating to the CRA or tax filing:
- Report it using the “report message” function in your inbox if you are using U of T Office 365/UTMail+. Otherwise, please report it to report.phishing@utoronto.ca.
- Do not follow any instructions in the email, delete it.
- Report the email to the Canadian Anti-Fraud Centre.
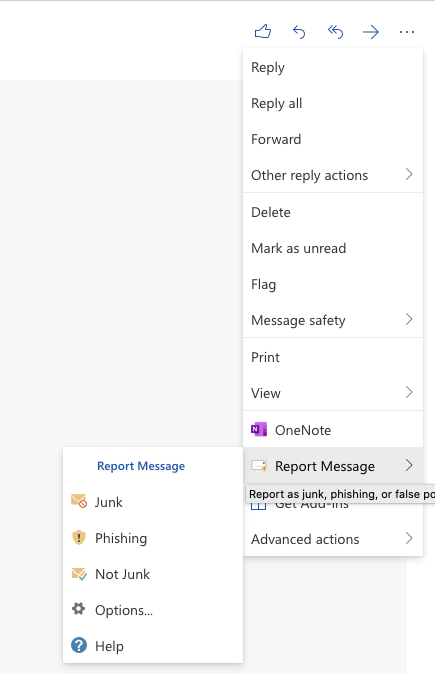
Here’re some tips to help you find the “report message” function in Outlook:
-
In the Outlook desktop app, the “report message” button is in the upper right corner of the menu bar:
- In the Outlook webmail, you can access the report function from two places:
-
From the preview pane:
-
From the email message:
Tax filers should be vigilant about tax-related communications either by phone, mail, text message or email. Never give out personal information, including financial information or login credentials to unidentified personnel.
When in doubt, always login to your CRA account through a trusted browser or call CRA’s Individual Income Tax Enquiries line at 1.800.959.8281.
For more tax-related scams and best practices to protect yourself, visit the CRA security site.
Remote Security Concerns
| DATE | Internal/External | Sites |
|---|---|---|
| 2020-03-30 | Internal | U of T ITS IT Preparedness |
| 2020-03-30 | Internal | Special Advisory on COVID-19 Phishing, Mar 19, 2020 |
| 2020-03-30 | Internal | CTSI Resources for Instructors |
| 2020-03-26 | External | Canadian government guidance |
| 2020-03-26 | External | UK government training |
| 2020-03-26 | External | SANS Security Awareness blog |
| 2020-03-26 | External | General guidance (cygenta.co.uk) |
Protect yourself against malware
Cyber attackers are constantly looking for new vulnerabilities in the software your devices use. When they discover vulnerabilities, they use special programs to exploit them and hack into the devices. Meanwhile, the companies that created the software are hard at work fixing them by releasing updates.
Here are some tips and resources to help protect your devices against malware while working remotely:
- Enable automatic updates on your devices. By ensuring your computers and mobile devices install these updates promptly, you make it much harder for someone to hack you. This rule applies to almost any technology connected to a network, including not only your work devices but Internet-connected TVs, baby monitors, security cameras, home routers, gaming consoles or even your car. If your computer is managed by your department, automatic updates may already be enabled.
- Install Microsoft System Center Endpoint Protection (anti-virus for Windows); it is available for no charge on University owned or leased equipment. See microsoft.utoronto.ca for more information.
- If you are using a work-provided computer remotely, be sure to only download and use products and software that are approved by your department.
- See this tip sheet on how to protect yourself from phishing attacks.
- Promptly report incidents to your IT personnel. See this list of contacts for details.
See more detail in this document.

Additional Security Matters articles about malware:
Protect yourself against personalized attacks
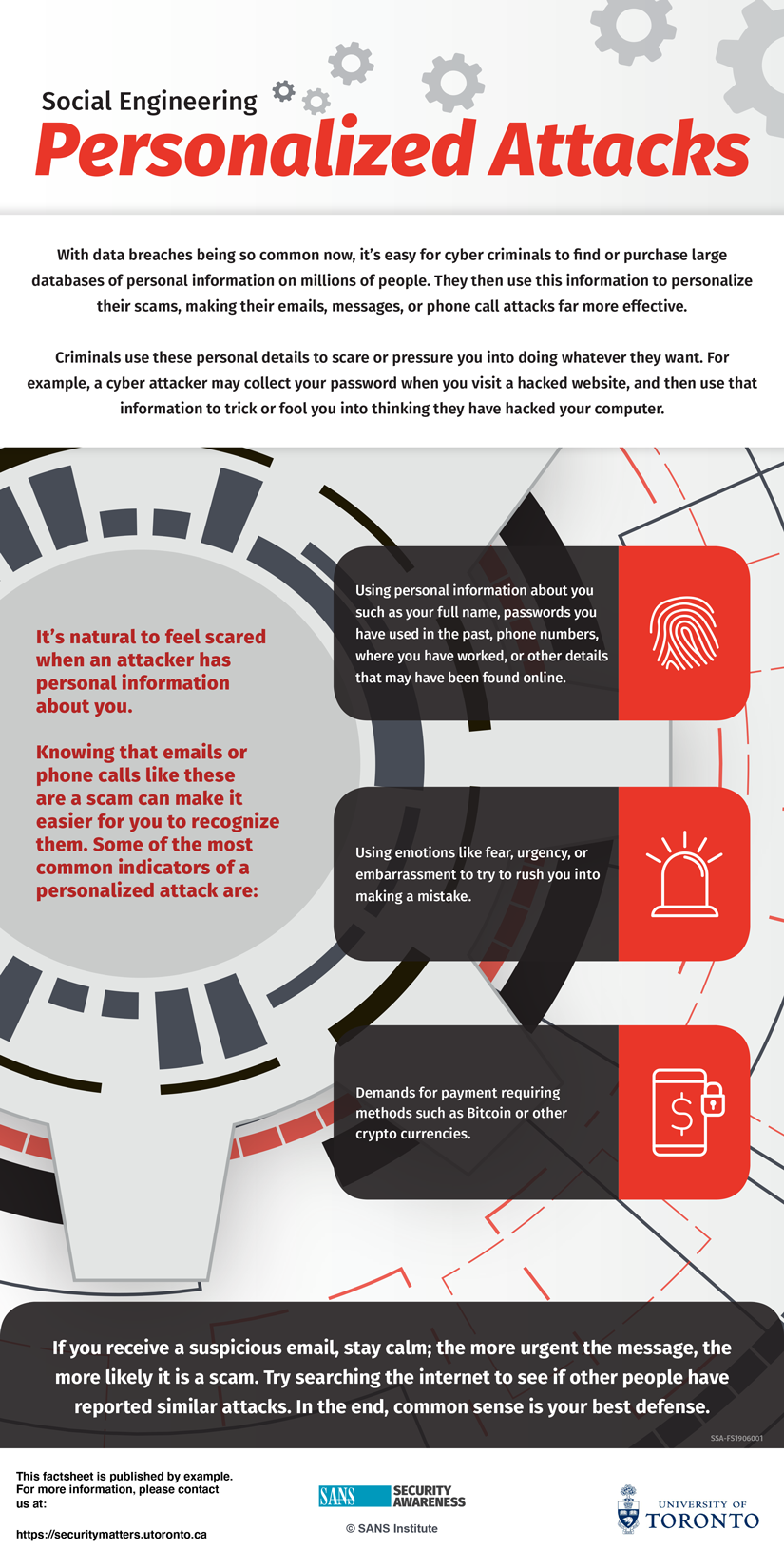
During this time of change and confusion, personalized cyber attacks are more common and have a greater success rate.
Here are some tips and resources to help you stay safe when working remotely:
- Get familiar with the different types of social engineering.
- Learn how to spot a phish! The best offence is a good defence!
- Learn about the anatomy of a phish.
If you suspect a social engineering attempt, follow this checklist:
- Resist the rush: If someone pressures you to act quickly under pressure, it is most likely an attack.
- Recognize the ‘bag of tricks’: If something sounds suspicious or too good to be true, it probably is.
- Think before you click: Be cautious: One wrong move could infect your device and spread it to others.
- If you are not sure, ask: Ask your manager or your administrator if what you are being asked to do is unusual; ask through your normal methods.
- Do not respond unless you are certain: do not provide your phone number or respond to emails. Hang up the phone if you feel threatened.
- React quickly if you think your account / computer was compromised: change your password and contact your local IT department.
See more detail in this document.
Want to learn more about malware and its effect on the U of T community?
Here are some Security Matters articles on previous incidents that involve social engineering
March 19, 2020 – special advisory on phishing messages
In response to the rapidly changing COVID-19 situation, the University has seen an increase in targeted phishing attacks and scams. These attempts are becoming more sophisticated and polished.
Some of these messages are crafted to look like urgent appeals to help with COVID-19 responses or appear to have the signature of a senior leader at the University of Toronto. This includes messages seemingly from high-level University administrators, executives, and managers within academic and administrative units.
Recent targeted phishing attempts include:
- Requests for COVID-19 money donations or app downloads that look like information sharing;
- Warning messages that appear to come from leaders/managers stating that your email, library or other U of T email account is about to expire; and
- Requests from senior leadership asking for immediate help (“Are you available?”), followed up by an unusual request (“Can you go get me some gift cards?”).
Be aware of incorrect email addresses and subject lines with a sense of urgency, for example:
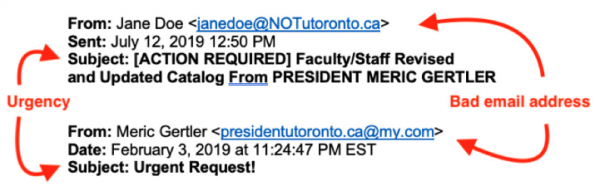
Sent: July 12, 2019 12:50 PM
Subject: [ACTION REQUIRED] Faculty/Staff Revised and Updated Catalog From PRESIDENT MERIC GERTLER
From: Meric Gertler
Subject: Urgent Request!
Note:
- The email addresses are not correct.
- The subject lines indicate urgency.
What to do if you suspect a phishing attempt:
- If you suspect your password may have been compromised, immediately change it;
- Report phishing messages to report.phishing@utoronto.ca; and
- When in doubt or if you opened an attachment that was provided in a phishing email, reach out to your local IT service desk immediately.
Thank you for your support as we work together to keep our tri-campus community members safe and University-related online information secure.
Thank you,
Isaac Straley
Chief Information Security Officer (CISO)

