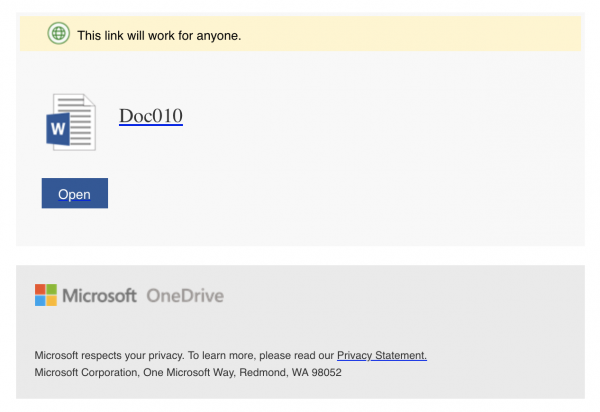
Recently, the University of Toronto (U of T) has seen an increase in targeted phishing attempts and attacks. These phishing attempts and attacks are becoming more sophisticated and polished. Some of these emails are crafted to look like urgent appeals for action from the signature of U of T leadership, including from high-level University executives, leaders and managers within academic and administrative departments. This includes fraudulent emails that appear to be sent from President Meric Gertler. U of T leaders’ signatures are being copied (from legitimate emails), their sign-off phrases and writing styles are also being mirrored and used by cyber criminals.
Recent targeting phishing attempts/attacks include:
- Urgent emails with memos attached from leadership
- Warnings that appear to come from leaders/managers that your email, library or other U of T account is about to expire
- Requests for immediate help (“Are you available?”), followed up by discussion (“Can you go get me some gift cards?”)
- Requests for changes to financial arrangements, especially banking or payment to creditor
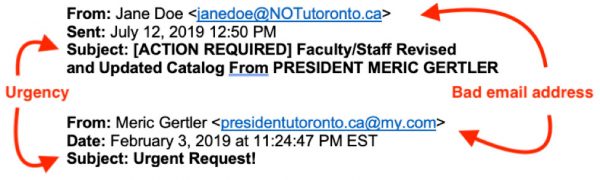
Look out for incorrect email addresses and a sense of urgency
What can you do if you suspect a phishing attempt/attack?
- If you suspect your password may have been compromised, immediately change it
- Please report phishing messages to report.phishing@utoronto.ca
- When in doubt, call or ask the sender in person to confirm the email was really from them
- If you opened an attachment that was provided in a phishing email, reach out to your local IT service desk immediately
Thank you for your support as we work together to keep all of us and our information safe and secure online.
Sincerely,
Isaac Straley
Chief Information Security Officer (CISO)