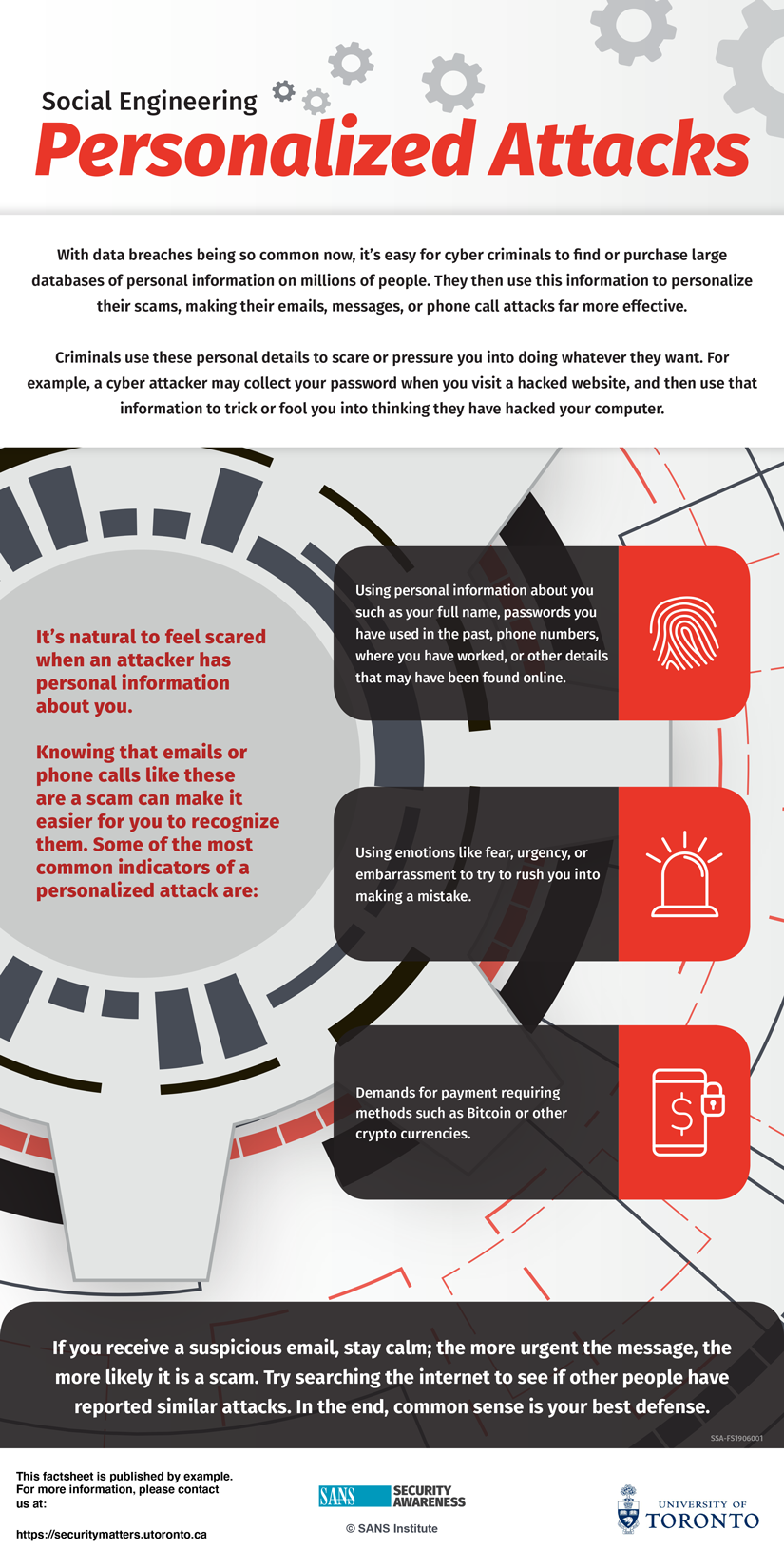
During this time of change and confusion, personalized cyber attacks are more common and have a greater success rate.
Here are some tips and resources to help you stay safe when working remotely:
- Get familiar with the different types of social engineering.
- Learn how to spot a phish! The best offence is a good defence!
- Learn about the anatomy of a phish.
If you suspect a social engineering attempt, follow this checklist:
- Resist the rush: If someone pressures you to act quickly under pressure, it is most likely an attack.
- Recognize the ‘bag of tricks’: If something sounds suspicious or too good to be true, it probably is.
- Think before you click: Be cautious: One wrong move could infect your device and spread it to others.
- If you are not sure, ask: Ask your manager or your administrator if what you are being asked to do is unusual; ask through your normal methods.
- Do not respond unless you are certain: do not provide your phone number or respond to emails. Hang up the phone if you feel threatened.
- React quickly if you think your account / computer was compromised: change your password and contact your local IT department.
See more detail in this document.
Want to learn more about malware and its effect on the U of T community?
Here are some Security Matters articles on previous incidents that involve social engineering
