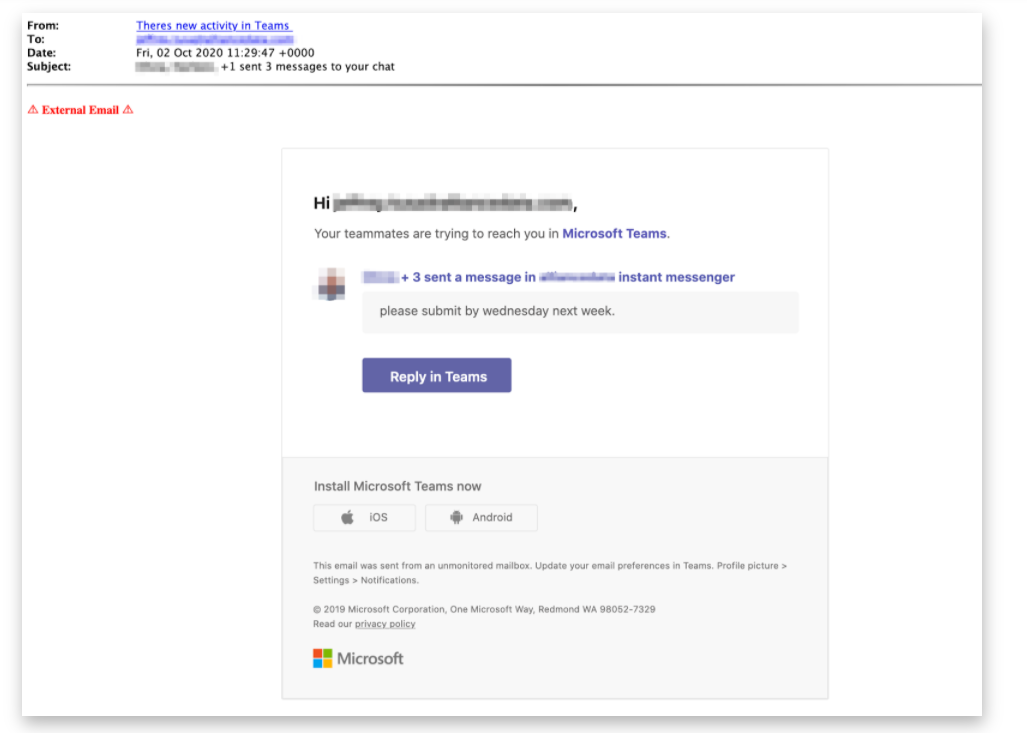
Microsoft (MS) Teams users should be weary of an impersonation phishing attack that is currently circulating. The attack mimics message notifications from the popular communication platform in order to steal Office 365 credentials from unsuspecting users.
The phishing email is usually sent from the display name, “There’s new activity in Teams,” which gives the appearance of a legitimate automated notification from the MS Teams platform. The email falsely notifies the recipient that they have unread messages and prompts them to respond by clicking on the “Reply in Teams” button embedded in the email.
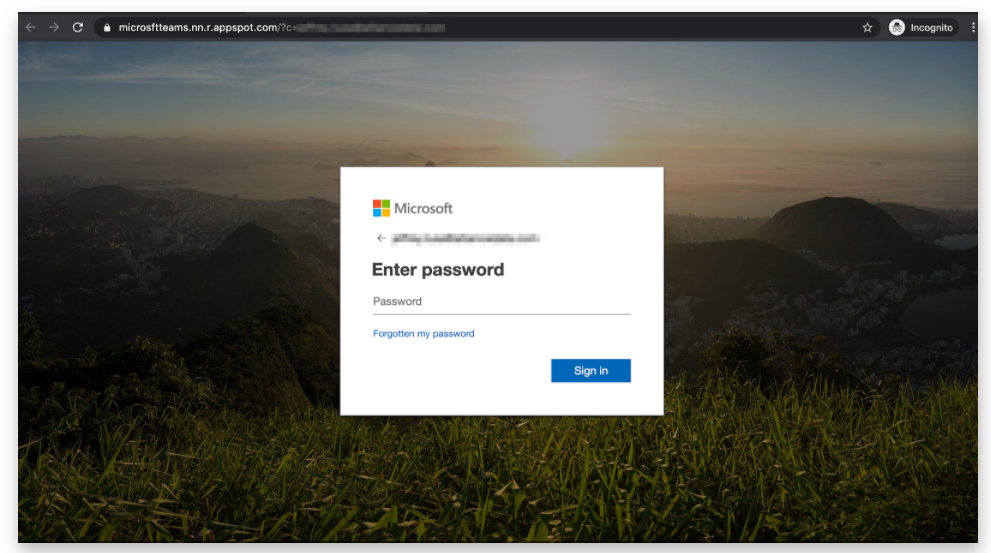
The user is then taken to a fake Microsoft login page where they are prompted to enter their credentials before being able to view the message. These fake Microsoft login pages are said to be well-crafted and therefore very convincing to the end user. Some have even been reported to contain the name “microsftteams” in the URL.
Users can protect themselves from this attack by:
- Not clicking on link/button in the email if you are unsure. Instead, go directly to the MS Teams app, or log into Teams via your web browser, to read any messages. If the message in the app or browser does not replicate the message notification received by email, then it is highly likely the email was a phishing attempt.
- Ensuring multi-factor authentication (MFA) is set up for their Office 365 account; for University of Toronto faculty and staff, this is UTORMFA. For more information on how to set up UTORMFA, please visit: https://isea.utoronto.ca/services/utormfa/.
If you suspect you have received a phishing email like the one described here, please report it to report.phishing@utoronto.ca.

