Blog

Mark your calendar for Data Privacy Day 2022!
December 10, 2021
Data Privacy Day is celebrated worldwide every year on Jan. 28 to raise awareness about technology and privacy rights, including the importance of safeguarding our personal information. The Information Technology Services (ITS) division is leading a Data Privacy Day 2022 campaign to raise awareness and educate the University of Toronto (U of T) tri-campus community ...

Building a security-aware culture
December 6, 2021
The University of Toronto (U of T) has partnered with Canadian Internet Registration Authority and ORION to pilot a Information Security Awareness Training platform for delivering information security awareness courses. “The Information Security Awareness Training pilot is part of our larger efforts to build a security-aware culture across the University and equip staff, faculty and students with the knowledge needed to ...
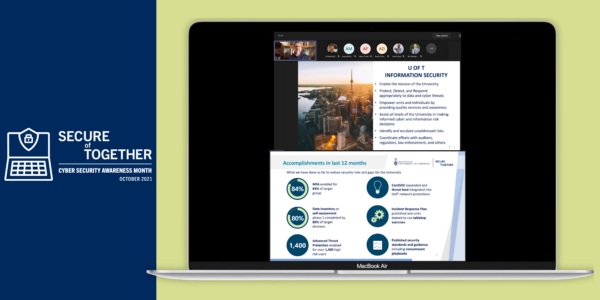
Cyber Security Awareness Month 2021 recap: Staying secure together
November 30, 2021
Believing that cyber security is a shared responsibility, the University of Toronto (U of T) community celebrated another Cyber Security Awareness Month (CSAM) this October. CSAM is an internationally recognized annual campaign that aims to educate individuals and institutions about the ever-changing field of cyber security and encourage best security practices. For CSAM’s 10th anniversary, ...

‘Tis the season to shop safe online
November 26, 2021
The holiday season is a lucrative time for online retailers and a vulnerable time for online shoppers. As many people take advantage of holiday deals and shop online, hackers take advantage of this time of the year to steal sensitive and confidential information. With the increased number of phishing attacks in recent weeks, it’s important ...

New wave of phishing attacks
November 23, 2021
Access to a diverse range of data from sensitive personal information to confidential research data, has made the University of Toronto (U of T) a popular target for various cyber-threats including phishing. Last week, more phishing attempts were reported as targeting the U of T community. The rising occurrence of phishing campaigns should serve as ...

Surge of phishing attacks at the University of Toronto
November 4, 2021
Social engineering is designed to evade common security setups by targeting the people inside organizations — relying on human error as the weak link. While hackers’ approaches behind social engineering may differ in form, their goals are all very similar: identity theft, data breaches, ransomware attacks and more. Phishing, one of the most popular forms ...

Beware of ‘COVID-19 Support Team’ phishing email
November 2, 2021
The battle against phishing attacks is an ongoing, daily task. Though we are equipped with highly-sophisticated and advanced tools for protection, hackers retaliate by evolving their techniques to evade these protections. It is important to continually educate ourselves and maintain awareness about phishing attacks to ensure our individual and institutional data remains protected. Hackers use ...

Employee perspectives: What you need to know about dealing with information security incidents
October 29, 2021
The University of Toronto’s (U of T) Information Security Incident Response Plan is available to help information technology (IT) managers, non-IT unit leaders and other employees handle security incidents effectively. We interviewed three Information Security directors to ask what we need to know about the plan and how it can help you deal with security ...

U of T community: Watch out for payroll fraud phishing email
October 27, 2021
Phishing has become one of the most popular subsets of social engineering. It is likely that most people have received an email urging action on an unknown link or attachment to prevent being ‘locked out of your accounts’. According to the 2021 Data breach Investigations Report (DBIR) by Verizon, 36 per cent of online breaches ...

Data classification: Using a risk-based approach for data protection
October 27, 2021
Most of us work with data on a day-to-day basis; the data we handle range from blog posts, course material and internal reports to personal information and health records. Not all data are created equal – while press releases and blogs are meant for public consumption, personal information and health records are extremely sensitive and ...
