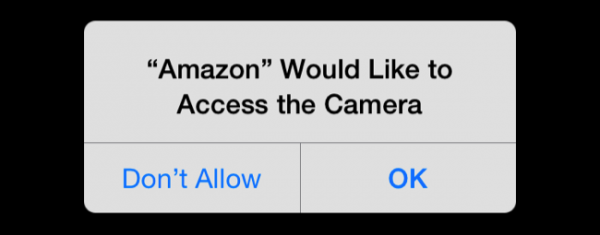
It’s important to pay attention to what you’re installing on your mobile device and the kind of permissions you enable, especially when granting access to your microphone or camera.
You should audit your phone regularly to verify that your apps only have access to the parts of your phone they need in order to function. You may even want to consider deleting some apps since studies show that out of 160,000 free Android apps more than 55 per cent of trackers tried to extract user location, while 30 per cent accessed the device’s contact list. A 2015 analysis of 110 free iOS mobile apps revealed that 47 per cent shared geo-coordinates and personally identifiable information with third parties.
After installing an app, you’re typically asked for permission to access specific hardware and software on your phone in order to function. Many apps ask for permission to access private channels, such as your camera, contacts, microphone, text messages and external storage.
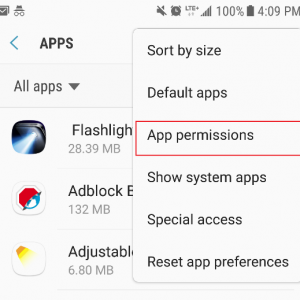
To check and modify your Android phone’s app permission settings, go to “settings” then “apps” and then use the top-right dropdown menu button to select “app permissions.”
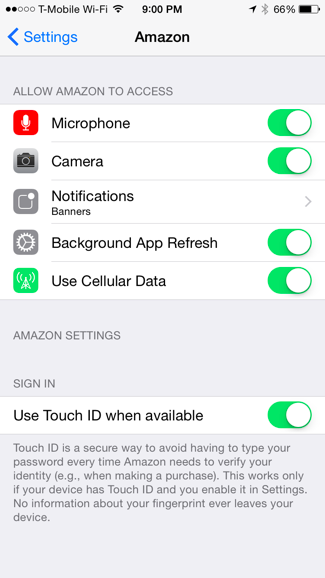
For iPhone users, simply navigate to “settings” then “privacy.” From here, you can view a list of your phone’s apps. Tap on any app to bring up a list of its permissions. Click the toggle next to each permission to enable or disable access.
Learn more about how to stay safe online and other related information security news.
To help you distinguish between typical vs. potentially risky access permissions, view the list below.
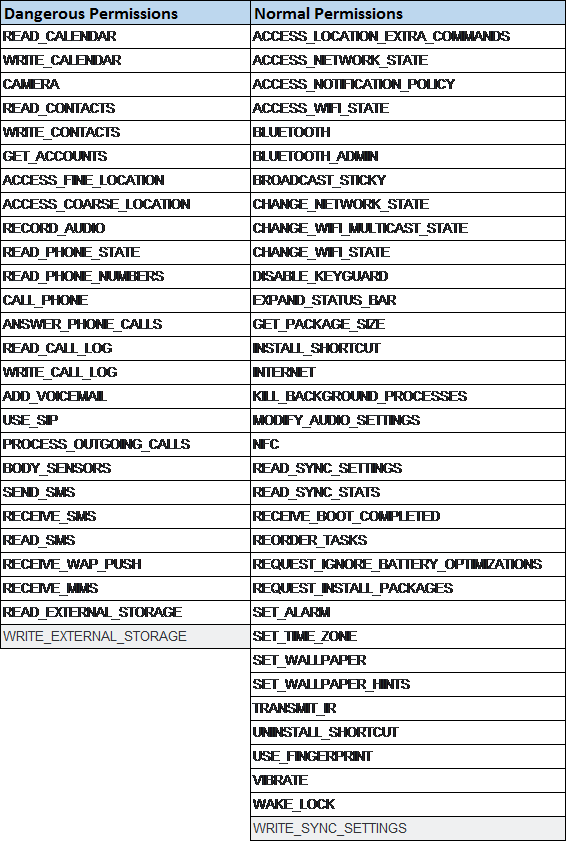
Normal permissions refer to typical mobile phone functionality, while dangerous permissions can intrude into your day-to-day interactions. For example, a game may request access to your calendar or contact list, despite their irrelevance towards functionality, so it’s important to deny these requests.




