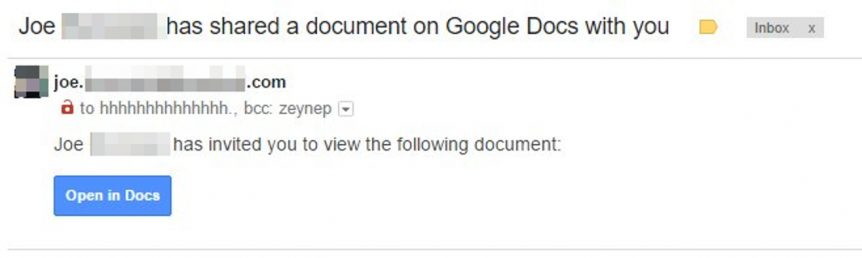
It’s four o’clock in the afternoon on a Thursday. You’re over the work week hump, vacation day tomorrow, maybe. The phone buzzes. It’s Gmail, letting you know that your friend Joe has invited you to edit a Google Doc. You open the invite and click on the big blue “Open in Docs” button like you’ve done a thousand times before. A window pops up telling you that ‘Google Docs’ would like permission to “read, send, delete and manage your e-mail” and “manage your contacts.” Annoying. Did you clear your cache recently or something? You click “allow” because it’s already 4:30 and you just want to see what’s going on in this doc before you go home; tomorrow you’ll attack whatever this document is. Weird. Instead of taking you to a doc the last box you clicked on took you back to your Gmail inbox. Now twenty of your friends are texting you wondering why you’re inviting them to edit a Google Doc. This is bad.
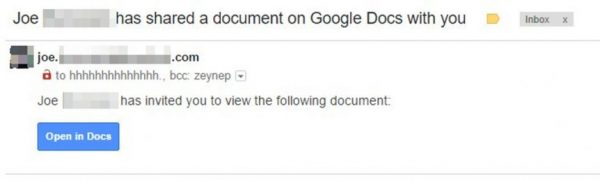
This scenario might be familiar to one million Gmail users who had their accounts hacked on Thursday by a sophisticated phishing scam, a malicious e-mail designed to trick them into giving a hacker access to their inbox. The worst part? Despite Google’s massive security budget, it came down to those users making a decision to click on a few links, links that under normal circumstances should have been trustworthy.
Just got this as well. Super sophisticated. pic.twitter.com/l6c1ljSFIX
— Zach Latta (@zachlatta) May 3, 2017
Phishing is tricky like that. The software industry spends billions of dollars on their security budgets, we can all use two factor authentication, complex passwords and encrypted traffic over SSL – all great defenses against online criminals. However, when it comes your inbox the best line of defense against a phish is a critical eye for e-mail.
Many criminals know this, which is why they send e-mails at 10am on a Tuesday morning or at 3pm on a Thursday afternoon. They want to catch you when you’re working hard and aren’t always thinking clearly as you trudge through the work week.
“The best line of defense against a phish is a critical eye for e-mail.”
The first question you should ask yourself whenever you get an e-mail with a link or file attachment is “Was I expecting this?” chances are if you work with someone they are going to tell if that they are sending you a file or a link before they send it to you. If you get an e-mail with a link or attachment you weren’t expecting, send a text message or call that person to confirm to origin of the message.
Treat e-mail with links or files attachments like strangers at your door. You wouldn’t open your door to strangers, so don’t click on any links or open any files without figuring out first if they are who they say they are. Use your best judgment and it shouldn’t be too much work. Remember if your e-mail does get hacked it is going to take way longer to wrestle back control of your account. Taking 30 seconds before opening something untrustworthy might save you a few hours and some heartache later.
“The first question you should ask yourself whenever you get an e-mail with a link or file attachment is “Was I expecting this?“”
Many phishing attacks are given away by who they are sent from: always check the ‘from’ and ‘to’ address on e-mails with files and links. You’ll notice that the google doc was addressed to “hhhhhhhhhhhhh@gmail.com”, weird right? Odd traits, unofficial addresses and bizarre typos are usually the a good sign that someone is trying to trick you with an e-mail. This isn’t a ‘silver bullet’ though. Online criminals might imitate a friendly e-mail address using a technique called “spoofing” where they imitate an e-mail address you trust. If a hacker is hoping you’ll click on a malicious link or open an infected file, then they can send you an e-mail from justin.trudeau@canada.ca, because they don’t need you to reply!
Finally, you should check out https://securitymatters.utoronto.ca/phish-bowl/ if you get a suspicious e-mail and want to see if the UofT Information Security Team has already caught similar offenders. We keep our phishbowl regularly updated with recent phishing attacks.
-Alex Dean Cybulski