Phish Bowl
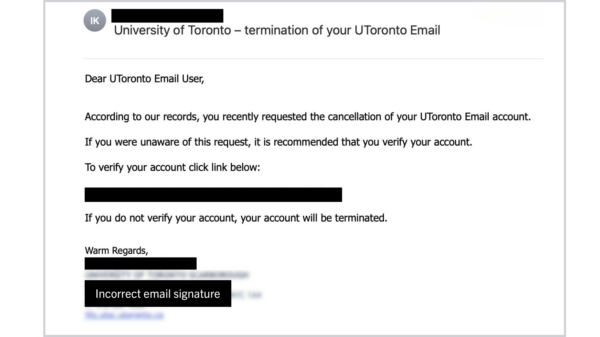
[Phish] University of Toronto – termination of your UToronto Email
November 3, 2023
Image of spoofed web page Description of the phish This phishing email attempts to steal the user’s login credentials by providing false information about their UTORid being filed for deactivation. The email contains a link to a web page spoofed to look like a U of T web page. The URL mentioned in the email ...

[Phish] Qishing message on LinkedIn
October 13, 2023
Description of the phish This is qishing, a social engineering tactic where malicious actors use QR codes to steal information from unsuspecting recipients. This message was sent to U of T community members via LinkedIn. How to protect yourself If you receive an unsolicited QR code, do not scan the code as it could be ...
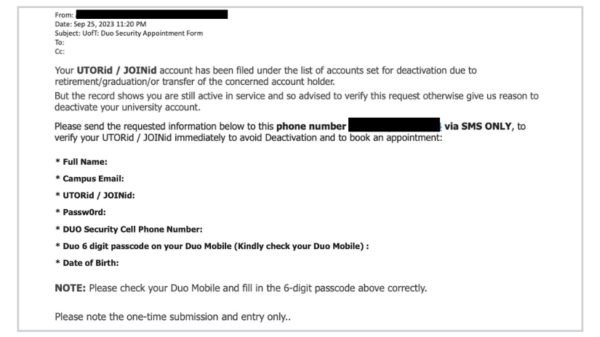
[Phish] UofT: Duo Security Appointment Form
October 2, 2023
Description of the phish This phishing email attempts to steal personal information, login credentials and Duo one-time passcodes by providing false information about the user’s UTORid/JOINid being filed for deactivation. How to protect yourself If you receive a Duo, UTORMFA or any other MFA notification that you did not initiate, do not approve the request. ...

[Phish] (Attn user.name) | 2 Factor Authentication (2FA) Outdated Today | Friday-September-2023 06:53 AM
September 18, 2023
Details: Subject: (Attn user.name) | 2 Factor Authentication (2FA) Outdated Today | Friday-September-2023 06:53 AM Microsoft 2FA Policy Dear user , Your authenticator session is expiring today, Kindly re-authenticate to avoid being locked out of your email account. Quickly Scan below QR Code with your Smartphone camera to re-authenticate your password security. *malicious QR code* ...
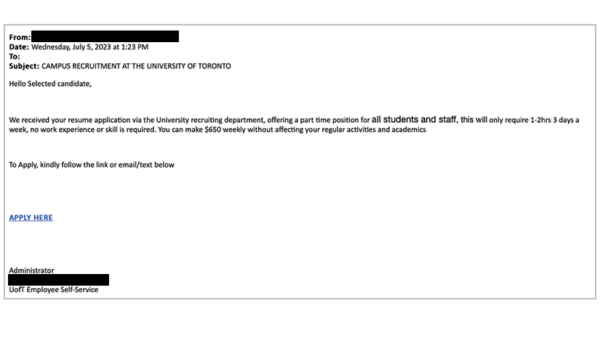
[Phish] CAMPUS RECRUITMENT AT THE UNIVERSITY OF TORONTO
July 27, 2023
Details: Subject: CAMPUS RECRUITMENT AT THE UNIVERSITY OF TORONTO Hello Selected candidate, We received your resume application via the University recruiting department, offering a part time position for all students and staff, this will only require 1-2hrs 3 days a week, no work experience or skill is required. You can make $650 weekly without affecting ...
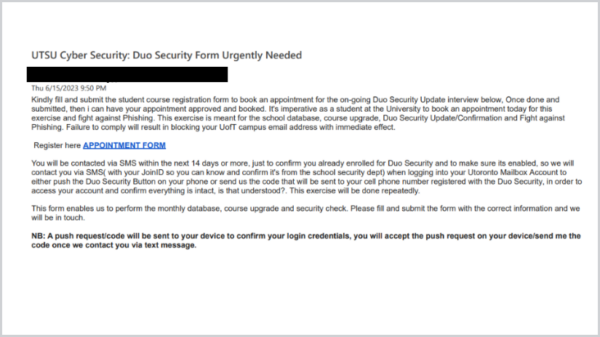
[Phish] UTSU Cyber Security: Duo Security Form Urgently Needed
July 5, 2023
Details: Subject: UTSU Cyber Security: Duo Security Form Urgently Needed Kindly fill and submit the student course registration form to book an appointment for the on-going Duo Security Update interview below, Once done and submitted, then i can have your appointment approved and booked. It’s imperative as a student at the University to book an ...
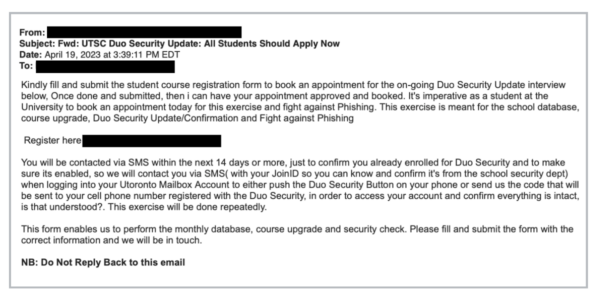
[Phish] UTSC Duo Security Update: All Students Should Apply Now
April 25, 2023
Details: Subject: UTSC Duo Security Update: All Students Should Apply Now Kindly fill and submit the student course registration form to book an appointment for the on-going Duo Security Update interview below, Once done and submitted, then i can have your appointment approved and booked. It’s imperative as a student at the University to book ...
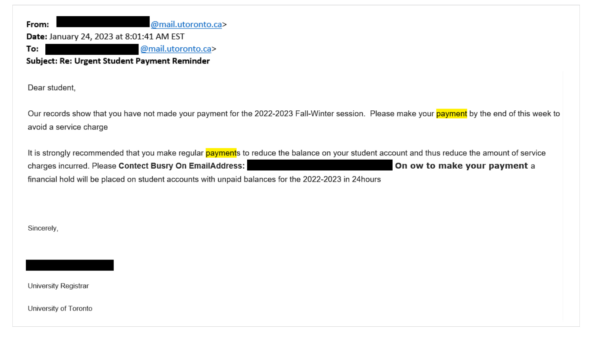
[Phish] RE: Urgent Student Payment Reminder
January 26, 2023
Details: Subject: RE: Urgent Student Payment Reminder Dear student, Our records show that you have not made your payment for the 2022-3023 Fall-Winter session. Please make your payment by the end of this week to avoid a service charge It is strongly recommended that you make regular payments to reduce the balance on your student ...
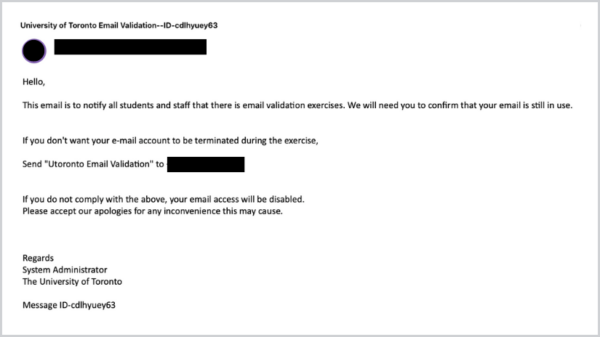
[Phish] University of Toronto Email Validation–ID-cdlhyuey63
November 3, 2022
Details: Subject: University of Toronto Email Validation–ID-cdlhyuey63 Hello, This email is to notify all students and staff that there is email validation exercises. We will need you to confirm that your email is still in use. If you don’t want your e-mail account to be terminated during the exercise, Send “Utoronto Email Validation” to {malicious ...
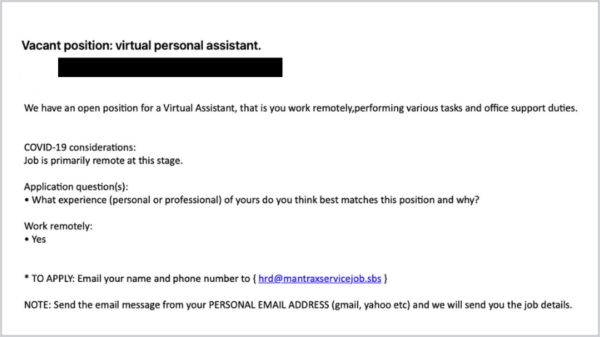
[Phish] Vacant position: virtual personal assistant.
May 30, 2022
Details: Subject: Vacant position: virtual personal assistant. We have an open position for a Virtual Assistant, that is you work remotely,performing various tasks and office support duties. COVID-19 considerations: Job is primarily remote at this stage. Application question(s): What experience (personal or professional) of yours do you think best matches this position and why? Work ...
