
This section of the website is intended for University of Toronto IT Professionals and Staff who are responsible for IT operations of their division or department.
You are team “blue”
You have the knowledge to protect data in your care from security attacks OR to let others know when there is a problem. As part of the U of T “BlueTeam” follow the basic tenets of CIA:
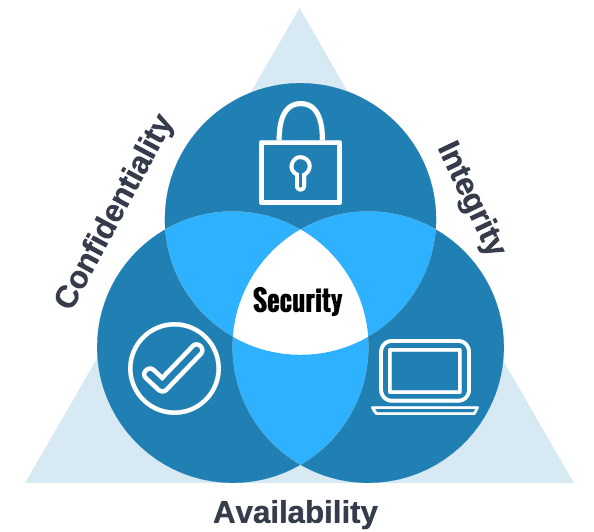
Confidentiality
Integrity
Availability
Current Highlighted Topics
Securing the Code – OWASP Top Ten
The primary aim of the OWASP Top 10 is to educate developers, designers, architects, managers, and organizations about the consequences of the most important web application security weaknesses. The Top 10 provides basic techniques to protect against these high risk problem areas – and also provides guidance on where to go from here..
Highlights
- OWASP Top Ten Project
- Why is application security so hard? Read “No Silver Bullet: Essence and Accidents of Software Engineering” By Frederick P. Brooks, Jr.
- OWASP for Education Institutions
Responsible Data Disposal
The university’s “Information Security Guidelines” outline standards for responsible data deletion and disposal methods. It is recommended that all IT Professionals follow these guidelines for best practices.
What You Need to Know:
Vendor Obligation Management
When engaging a vendor for the procurement of an IT solution, it is critical to consider some key elements to ensure a secure integration. This is what we call vendor obligation management. It describes what the vendor needs to do to properly integrate into the U of T infrastructure and the minimum standards that should be met.
Engaging a Vendor Checklist:
Information Security Services
Access information security services offered centrally by Information Technology Services.
Top Services:
Additional Resources
Visit our resources page for more details.
